SoftComply Information Security Risk Manager User Guide
1. QUICK START GUIDE
- Create or choose a specific company-managed Jira Project you intend to use for Infosecurity Risk Management.
- Open the InfoSec Dashboard from the global apps page.
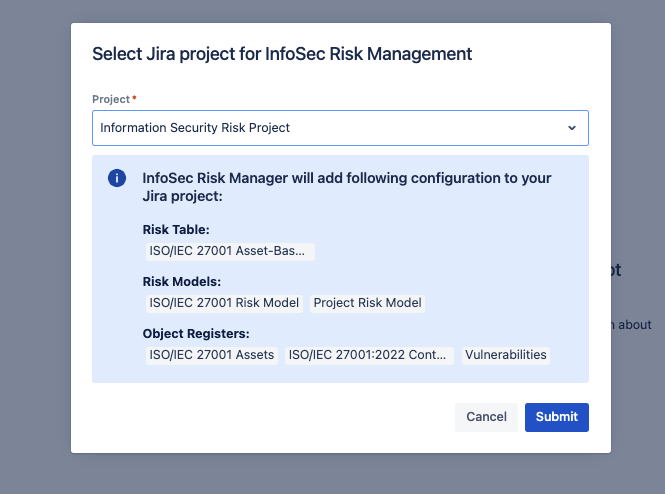
- Click on the “Set Up InfoSec Risk Management“ and choose the Jira project from the list of available projects.
- Next, you will see the setup overview (configuration that will be added to the project).
- Confirm the selection to enable the InfoSec Dashboard view.
- On top of the page you will find all related links (Risk Table for risk management, Controls and Assets Register links)
- The dashboard page provides overview of the risk management status, traceability information and ISO/IEC 27001 checklist.
- On the dashboard page you can also track your progress of implementing the ISO/IEC 27001 requirements.
2. MANAGING RISKS
Risk management for InfoSec risks is divided into 2 sheets and managed via the Risk Table view in the selected Jira project.
The risks can be accessed from the InfoSec dashboard (link in the header of the page) or directly from Jira project (Apps -> Risk Manager -> Risk Table).
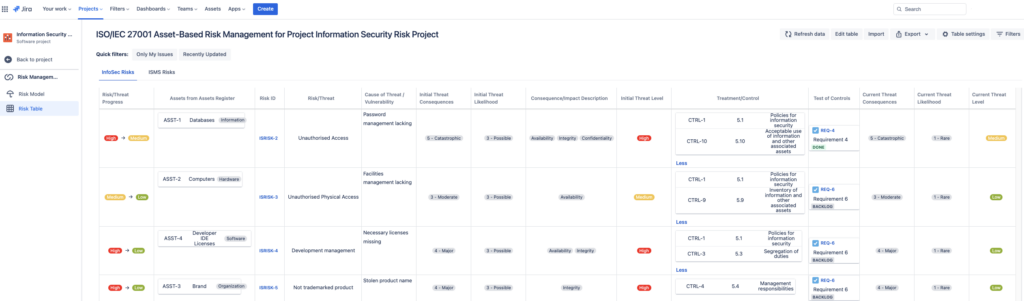
ISO/IEC 27001 Risk Table consists of 2 sheets:
- Asset-Based Risk Management Table (for your InfoSec Risks);
- Information Security Management System implementation project risks.
Read more about how to customize and operate the risk table from the Risk Manager Plus (Cloud) User Guide.
Risk models can be fully customized i.e. you can set up the risk acceptability criteria and risk characteristics and their descriptions based on your risk management process. The available risk models’ setup guide is also available in the Risk Manager Plus on Cloud User Guide.
3. MANAGING CONTROLS, ASSETS AND VULNERABILITIES
The InfoSec Risk Manager has 3 different Object Registers out-of-the-box:
- ISO/IEC 27001 Annex A Controls;
- Assets Register;
- Vulnerabilities Register.
Read mode about Object Register from the Risk Manager Plus on Cloud User Guide.
The structure and the data in the registers are fully customizable. The ISO/IEC 27001 Controls Register has the recommended structure for the Statement of Applicability document. You can therefore use this register to create and maintain your SOA document.
The two registers (Controls and Assets) are connected to the Risk Table (Asset-Based Risk Table) but you can configure the registers as you need.
We suggest to keep Controls in the register and link your risks to the controls to get adequate traceability information in your InfoSec Dashboard.
Since the traceability information in the Dashboard is pulled from the registers, the traceability information may end up incorrect when your Controls and Assets are not in these registers in the Jira project.
3.1. CVSS Metrics
The Common Vulnerability Scoring System (CVSS) Settings page in Jira allows you to manage the CVSS version used for assessing the characteristics and severity of software vulnerabilities. Follow these steps to navigate and configure the CVSS settings:
Accessing CVSS Settings
- Navigate to the CVSS Settings Page:
- On the Jira global menu open Risk Manager app page, locate the left-hand sidebar and navigate to Settings.
- Under the Integrations section, click on CVSS Settings. This will open the CVSS Settings page.
NOTE that CVSS Versions Are Not Backward Compatible:
Before changing the CVSS version, be aware that the current metrics will be reset. Your scores and CVSS vector values will remain unchanged until you reassign metrics to your vulnerabilities.
Changing the CVSS Version
- Locate the CVSS Version Dropdown:
- On the CVSS Settings page, find the dropdown menu labeled CVSS version.
- Select the Desired CVSS Version:
- Click on the dropdown menu.
- Select the desired CVSS version from the list. For example, the currently selected version is 4.0.
- Confirm Your Selection:
- After selecting the desired version, ensure to review any warnings or notices provided.
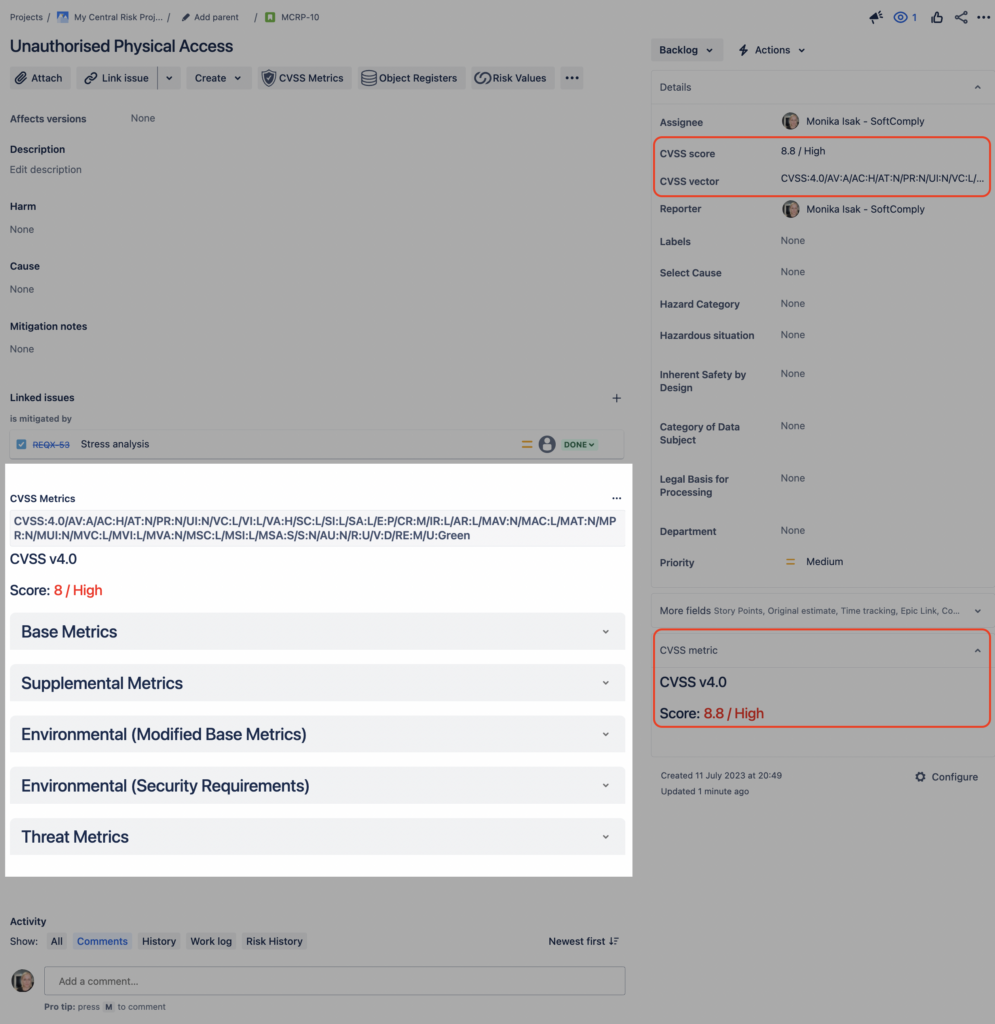
Configuring CVSS Vector and CVSS Score Field in Jira
The Common Vulnerability Scoring System (CVSS) Metrics page in Jira enhances your ability to monitor, prioritize, and manage security vulnerabilities within your Jira environment.
First, select the applicable CVSS version in the Risk Manager Plus Settings > CVSS Settings
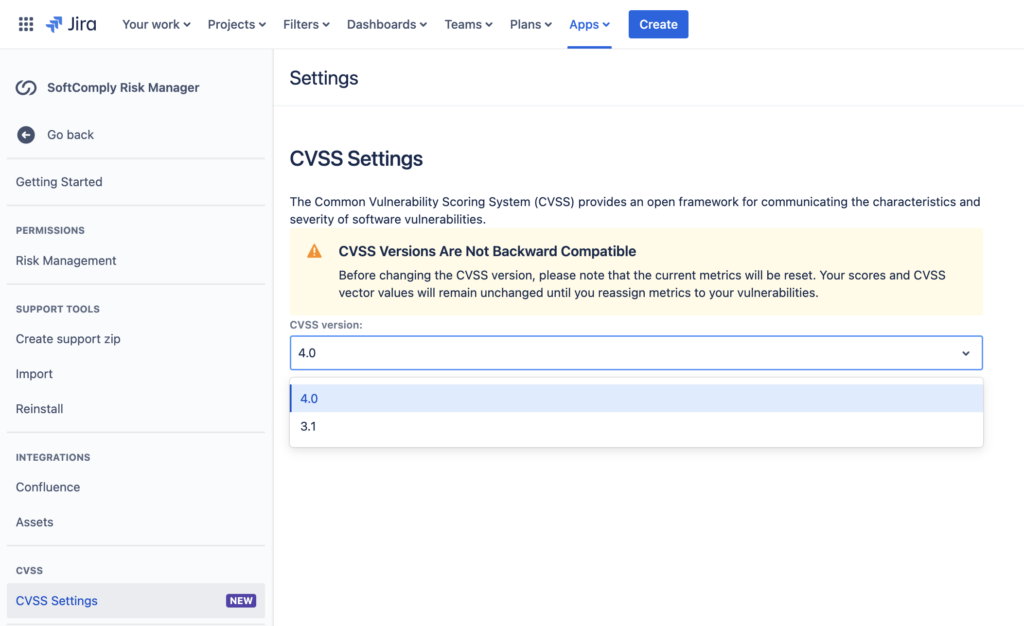
Go to Risk Manager Settings > CVSS Settings to enable the correct version
You will see the CVSS Metrics icon on the issue view top panel and you can open the assessment panel by clicking on the icon.
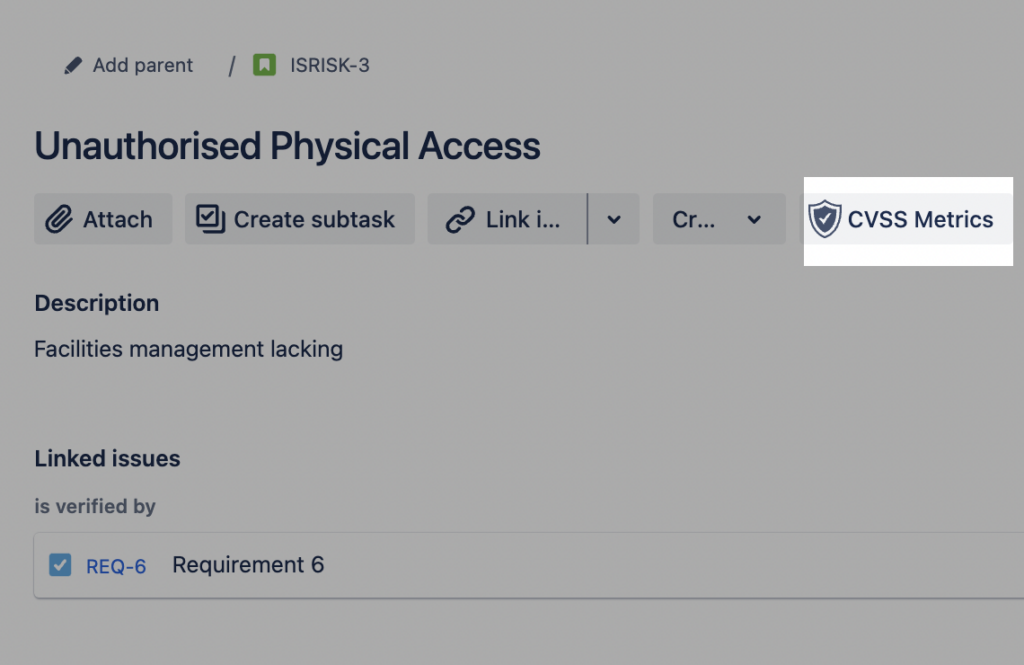
CVSS Metrics icon in an Issue view
Note – if you see a warning that the required field (CVSS vector) is missing, follow the steps below to configure the CVSS vector field.
Configure CVSS Vector/Score Field
- Navigate to Project Settings:
- From the Jira dashboard, navigate to the project where you want to configure the CVSS vector / CVSS score field.
- Click on Project settings in the left-hand sidebar.
- Access Issue Screens:
- In the Project settings, find and click on Issues → Screens. This will show a list of screens grouped by issue types available in your project.
- Select the screen:
- From the list of screens, select the one for which you need to configure the CVSS vector/score field. For example, if you want to configure it for a Bug or Vulnerability issue type, click on the respective screen.
- Add CVSS Vector and CVSS Score Field:
- Look for an option to Add field
- Search for CVSS vector / score in the available fields list.
- Select CVSS vector / score and add it to the issue type.
Verify Configuration
- Create or Edit an Issue:
- Create a new issue or edit an existing issue of the type you configured.
- Check if the CVSS vector / score field is now available in the issue form.
- View CVSS Metrics:
- Navigate back to the CVSS Metrics page.
- Verify that the warning message is no longer displayed and that the CVSS metrics are visible for the configured issue type.
Additional Notes
- Permissions: Ensure that you have the necessary permissions to configure fields and issue types in the project. If you do not have sufficient permissions, contact your Jira administrator for assistance.
- Field Context: Make sure that the CVSS vector field is added in the correct context for the issue type to ensure it is available where needed.
Using CVSS Fields in JQL Searches and Dashboards
Once the CVSS vector and CVSS score fields are configured, they can be effectively utilized in Jira for advanced searches and dashboard reporting. You can use Jira Query Language (JQL) to filter issues based on CVSS metrics, allowing you to create custom queries such as finding all issues with a specific CVSS score range or vector value. These fields can also be added to Jira dashboards as gadgets, providing a visual representation of th
4. PROJECT SETUP
4.1. Overview
Information Security Risk Management includes the following:
- InfoSec Dashboard with its features can be disabled/enabled from the Settings.
- Risks can also be managed when the InfoSec dashboard is disabled.
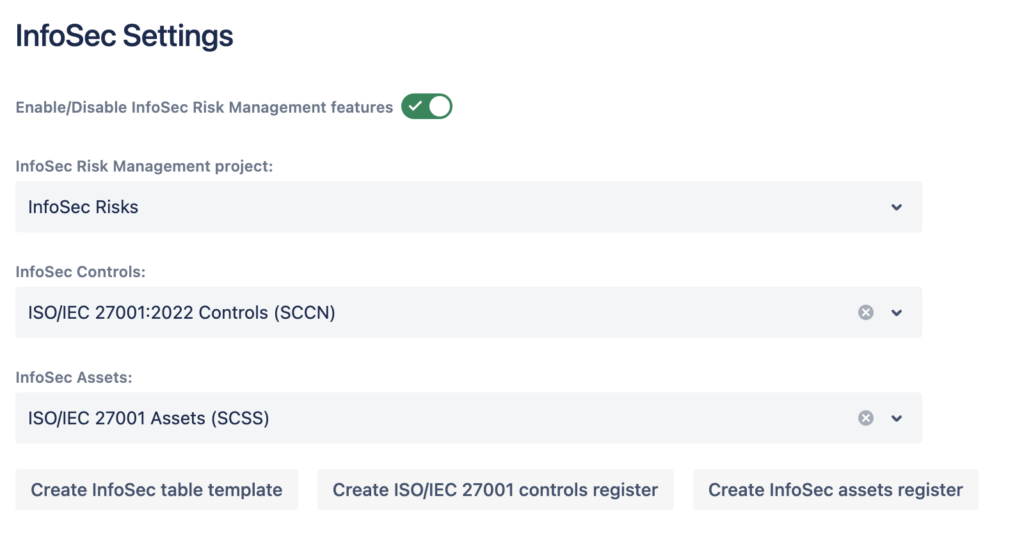
4.2. Settings
Users can change the three sections of the traceability (risk project, controls register, assets register) any time from the InfoSec Settings page in order to get a traceability overview between different objects.
4.3. Enabling the Information Security Risk Manager
To enable risk management in any Jira project you need to assign a risk model to it. You can assign a risk model to a Jira project from 2 different locations:
- from the Risk Models list (on global application page); or
- from the Jira project page (Enable Risk Management first).
You can add/remove additional risk models in the Jira Project settings.
NB! Use the Risk Table view for everyday risk management.
5. LIMITATIONS
Information Security Risk Manager application is a limited edition of the SoftComply Risk Management Plus application, with the following limitations compared to the Risk Manager Plus app.
Risk Models:
- 3 Risk Models are supported in the InfoSec Risk Manager app. The Risk Manager Plus supports an unlimited number of Risk Models.
- Risk Models cannot be added/removed in the InfoSec Risk Manager, only updating of Risk Models is allowed.
- 3 dimensional Risk Matrix is not supported in the InfoSec Risk Manager while it is supported in the Risk Manager Plus.
Risk Tables:
- 2 Risk Tables are supported in the InfoSec Risk Manager app. The Risk Manager Plus supports an unlimited number of different Risk Tables.
- Sheets in the Risk Tables of the InfoSec Risk Manager cannot be added or removed.
Object Registers:
- 3 Object Registers are supported in the InfoSec Risk Manager. The Risk Manager Plus supports an unlimited number of Registers.
Full comparison between the SoftComply Information Security & the Risk Manager Plus applications can be viewed here.
