Introduction
Hey there, brave souls navigating the wild seas of cybersecurity! 🌊
If you’ve ever embarked on the treacherous journey of implementing NIST Cybersecurity Risk Management, only to end up with a mountain of spreadsheets and a profound sense of existential dread, you’re not alone.
But fret not, for today, we dive into how you can actually make this work inside Jira Cloud. Spoiler alert: spreadsheets were not invited to this party!
You can also watch the implementation guide in our YouTube video here:
The Quest for Operational Glory
NIST guides you like a wise old wizard on what good cybersecurity management should look like. But when theory doesn’t translate into operational magic, it’s like being told you can have a unicorn, then being handed a broomstick.
We’re here to show you how to ride that unicorn (metaphorically, of course) using SoftComply Risk Manager Plus app on Jira Cloud. Who knew magic and cybersecurity could go hand-in-hand?
NIST CyberSecurity Framework 2.0: Beyond the Grandma’s Knit Club
The latest NIST Cybersecurity Framework 2.0 takes things up a notch. It’s no longer just about guarding the dungeon’s treasure, i.e., critical infrastructure. Now, it’s about managing risks across all levels of the kingdom, I mean organization. And, here’s the kicker: these levels need to be connected!
Goodbye, isolated spreadsheets! Hello, structured, multilayered risk models. Think of it as your very own cybersecurity lasagna.
Adventures at the System Level
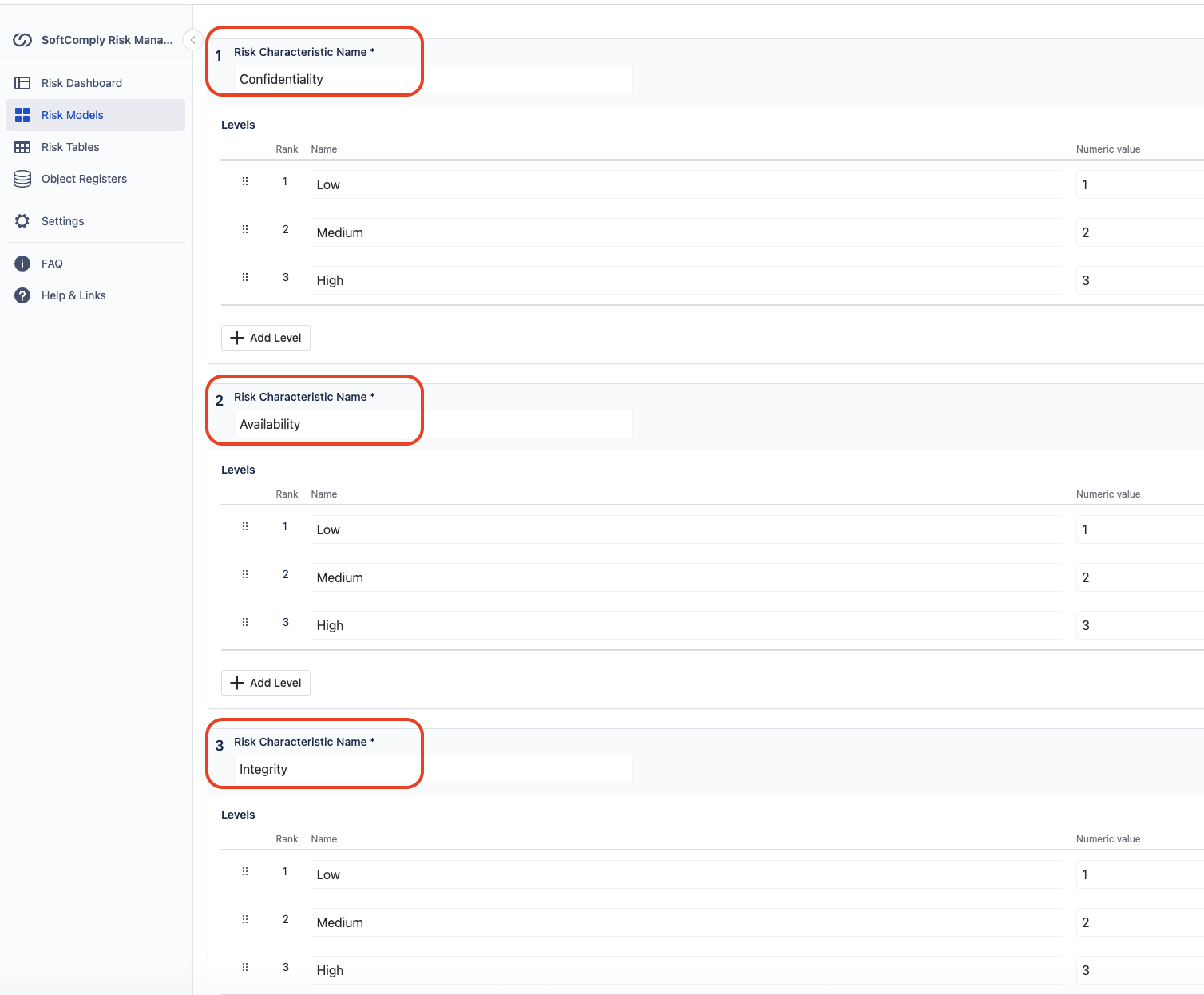
Let’s embark on our journey at the system level. This is the technical side – the nuts and bolts, the pixels and bytes. We focus on what might happen to a system’s Confidentiality, Integrity, and Availability (CIA). And no, these aren’t secret agents, but they are a secret sauce in cybersecurity thinking.
So next time someone asks, “Does this threat impact confidentiality?” know that it’s not someone asking if you’ll keep a secret. It’s about data impact!
Nested Risk Models
Inside the fabulous SoftComply Risk Manager Plus app on Jira Cloud, we use nested risk models to help you manage your cybersecurity risks.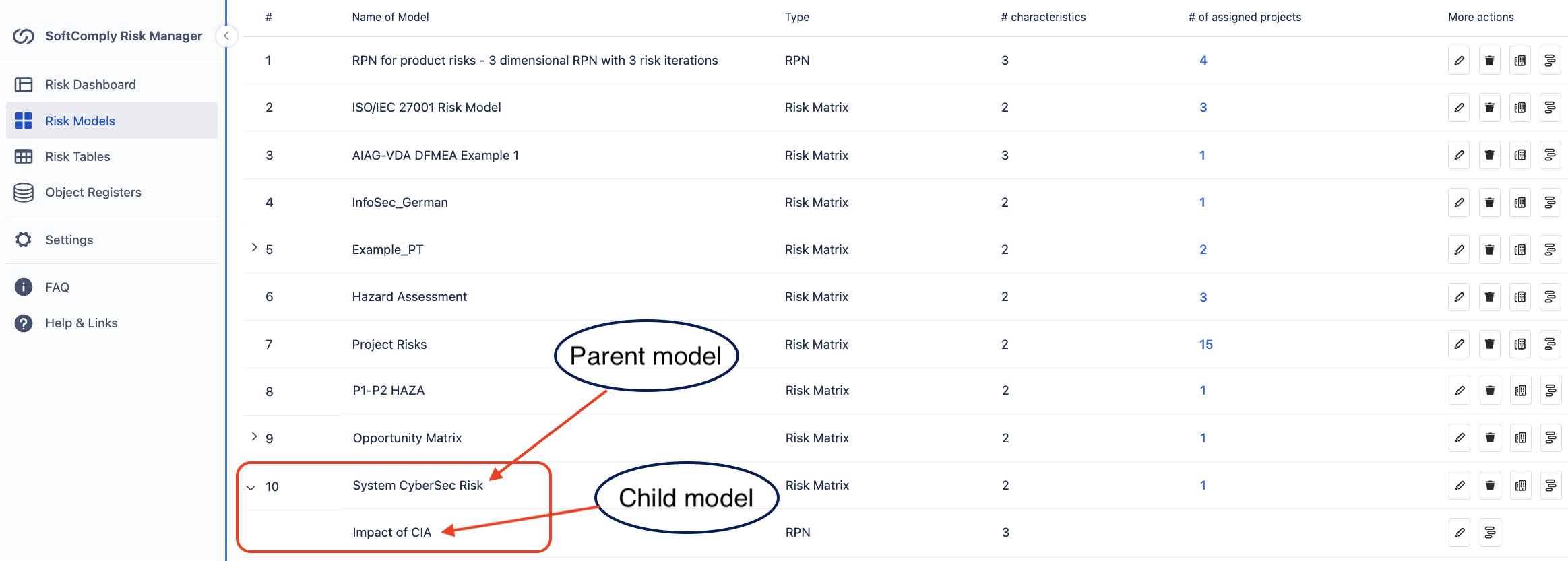
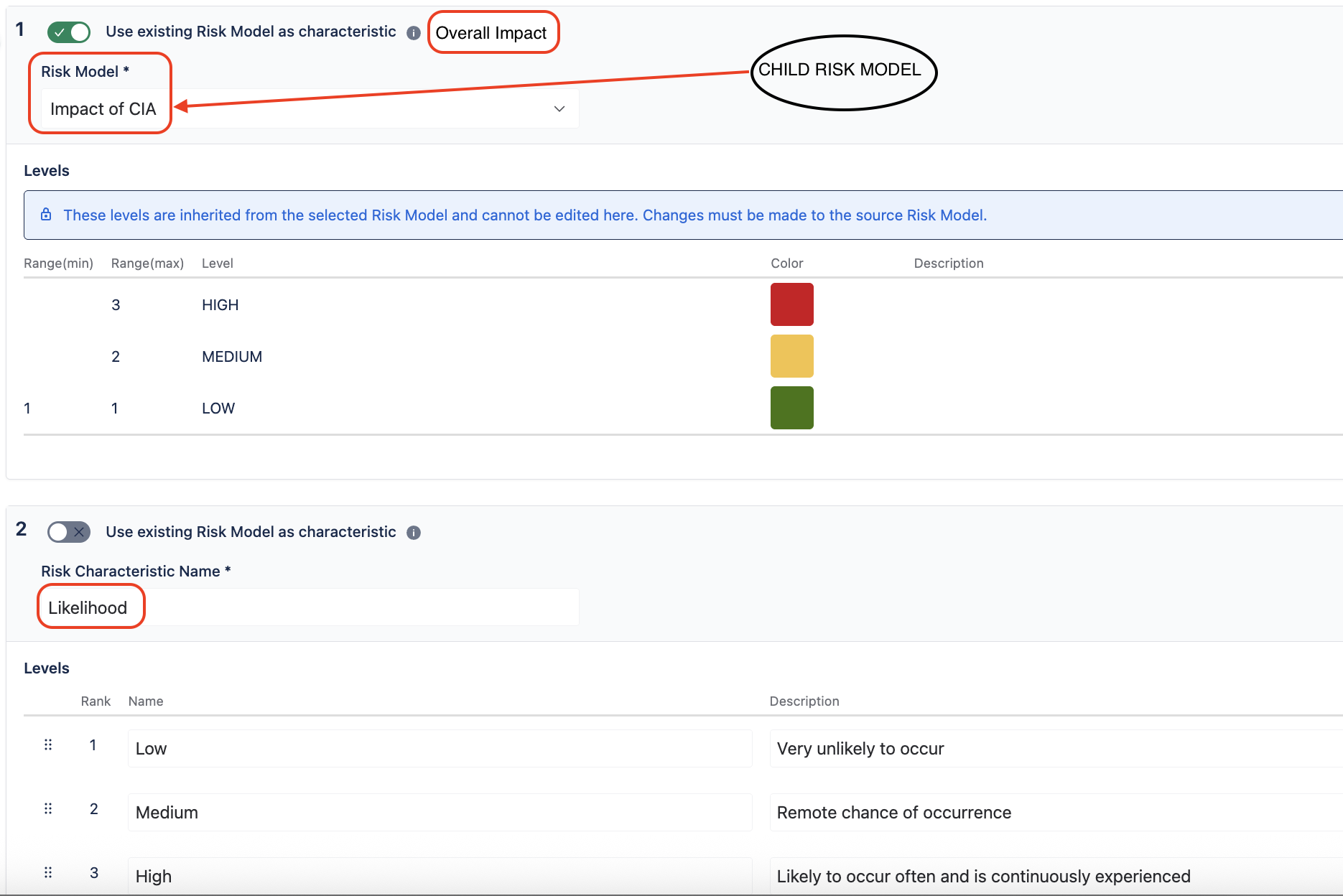
We’ve got a child model assessing CIA impacts with low, medium, high ratings.
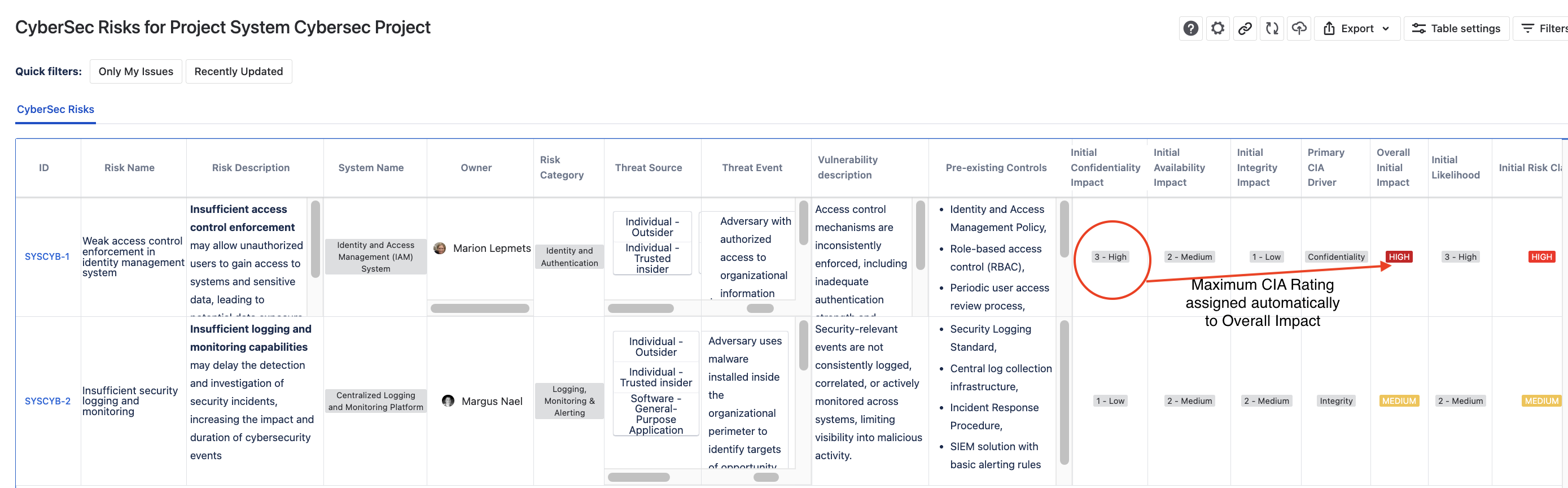
The model automatically assigns the maximum rating from the three of them that will be used on the parent risk model level as the Overall Impact of the risk.
Together with the Likelihood of the Threat, the parent model then uses the Overall Impact and Likelihood to find the Risk Class — a little family of cybersecurity goodness.
The Magic of Risk Registers
Ever heard of the risk register? Now imagine one that doesn’t need to be built from scratch.
In SoftComply Risk Manager Plus, you start with ready-made risk register templates aligned with NIST. Instead of typing everything manually, you can select threat sources, threat events, and controls directly from built-in NIST libraries.
The structure is already there – you simply choose what applies. It saves time, reduces errors, and keeps your cybersecurity risk register consistent. Isn’t it nice when the heavy lifting is already done for you?
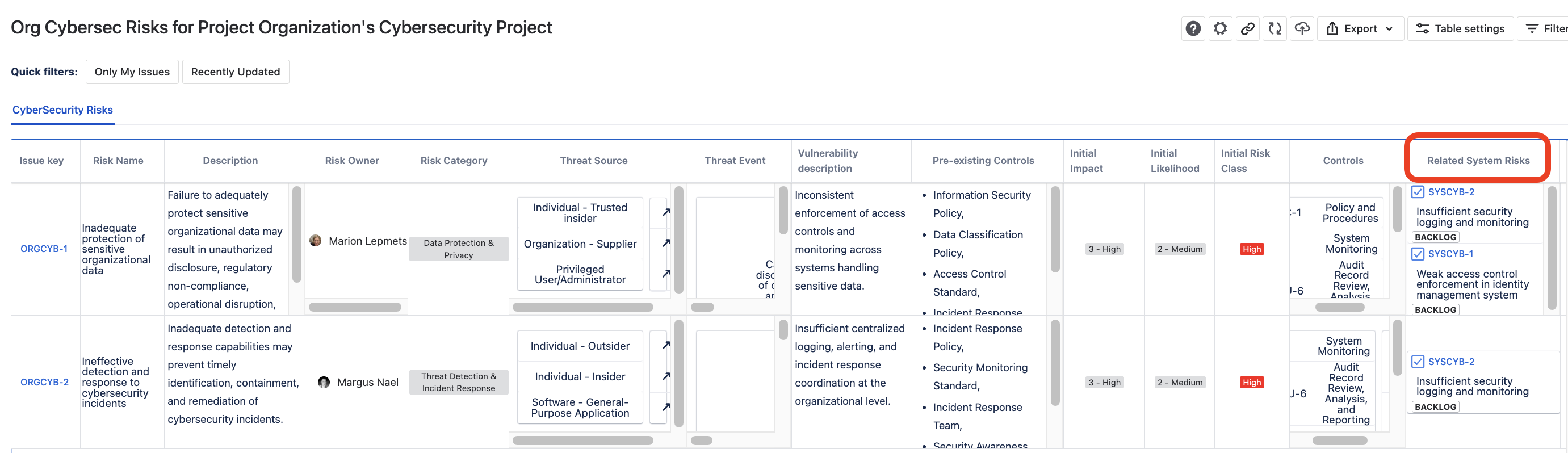
The Not-So-Isolated System Risks
In our tale, your system risks aren’t lone wolves – they’ve got packmates in the organizational risk clan.
Technical consequences roll up to business exposure, with a nifty vertical traceability. It’s like stacking LEGO blocks, only less likely to be stepped on barefoot.
Finale: Baseline and Approval of Cybersecurity Risk Review
Picture a risk review meeting. You’re pulling information seamlessly from Jira to Confluence, and just like taking a selfie, you capture a snapshot of the current state.
Once you’ve locked in this masterpiece, it’s ready for the world – or at least for the organization.
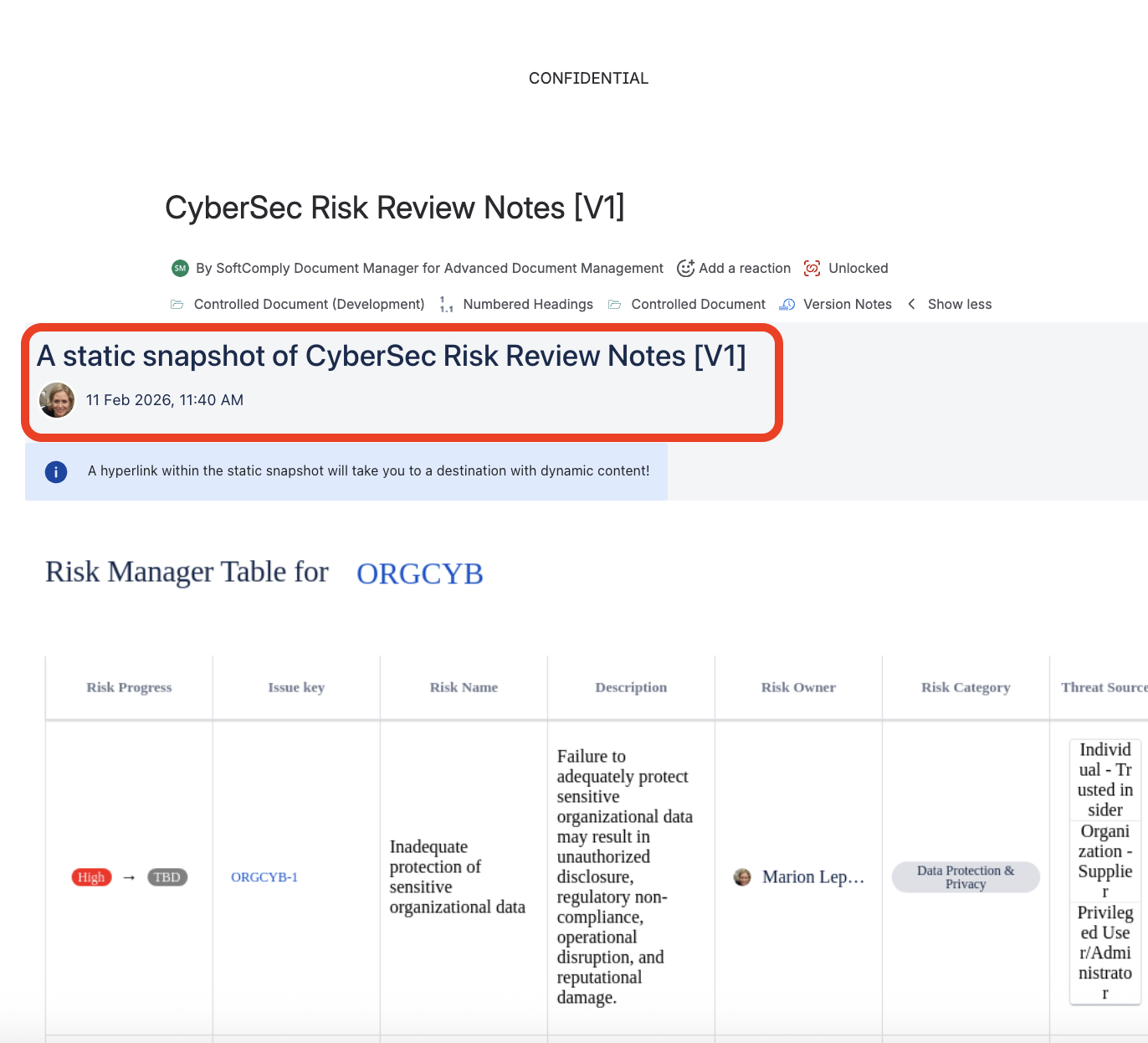
This is what auditable governance looks like, folks. All done inside Jira and Confluence.
Conclusion
So if you’re tired of wrestling with spreadsheets and are ready to implement NIST like a pro – without losing hair or sleep – look no further.
Book a call with us and let’s get your cybersecurity risk management into Jira.
Thanks for joining the ride, and remember, in the world of cybersecurity, not all heroes wear capes; some just have really good risk management documentation. Best of luck!