Being an ISO 27001-compliant company means that you protect your information assets and client data against possible data breaches. It supports your business growth as it builds trust in your company and your products.
In the hopes of achieving ISO 27001 compliance quickly, many companies purchase a huge ISO 27001 requirements checklist and templates for their ISMS. More often than not this “one-size-doesn’t-fit-all” solution turns out to be too much – your ISMS might only be a fragment of it.
Instead of starting from such an all-encompassing solution, start from what you have (your assets), possible risks related to them and how you can protect yourself against them (ISO 27001 controls). This approach will help you establish your actual ISMS scope, focusing on managing the risks of your information assets.
4 Steps to Start your ISO/IEC 27001 Compliance Journey
STEP 1: Identify your Assets (databases, systems and processes that include customer data, intellectual property, financial information, etc.);
STEP 2: Analyse the related threats and vulnerabilities for each asset;
STEP 3: Evaluate the potential likelihood and consequences of threats and vulnerabilities;
This step helps you find all the critical risks.
STEP 4: Select and apply suitable Control(s) for each Risk.
This step helps you create a Risk Treatment plan, which includes selecting and implementing applicable controls from the ISO/IEC 27001 list of controls.
How to manage Information Security Risks in Jira?
SoftComply Risk Manager Plus on Jira Cloud includes dedicated modules for information security risk management in Jira to support you in your compliance journey towards ISO 27001.
To fast-track your information security risk management, the app comes with a ready-made Risk Model for your information security risk assessment as well as an out-of-the-box Risk Register for your Asset-based Risk Management in Jira. The latter is a multi-sheet Excel-like spreadsheet where you can manage and link your assets to risks and ISO 27001 controls.
The Dedicated Modules for your information security risk management in the SoftComply Risk Manager Plus app are the following:
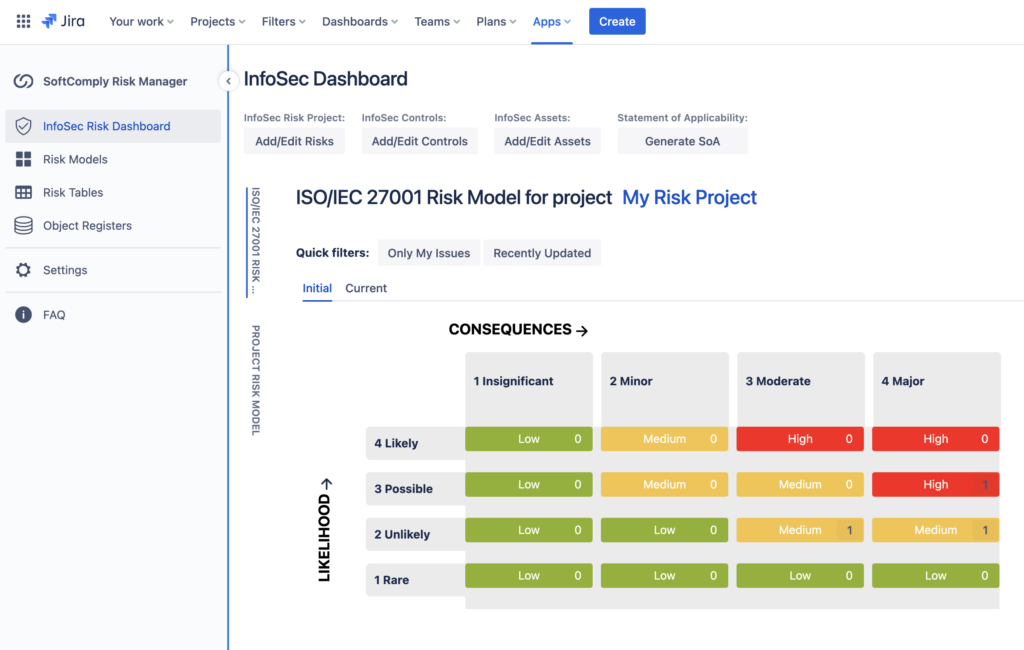
- The Information Security Dashboard provides you an easy way to monitor your progress towards ISO 27001 requirements. Here you can build a traceability matrix between the assets you have defined, the related risks for each asset that you have identified and the applicable controls from ISO 27001 that you have linked to the risks. This will help monitor the status of coverage between your assets, related risks and applicable controls.
- Object Registers for your Asset Management where you can define your organisation’s information assets, describe them and assign ISO 27001 controls to them. You can find the ISO 27001 controls already in the app as you install it.
- Last but not least, you can generate your Statement of Applicability directly from your Object Register or from your InfoSec Dashboard at any point in time or when you are ready for the audit.
How to Learn More
To learn more about Information Security Risk Management in Jira, feel free to try out the app or book a demo call the SoftComply team:





