Like with any compliance journey, you should first establish why you need to be compliant with a certain regulation. ISO 27001 certification is widely used to build trust and credibility with customers and stakeholders.
Similarly, in the Atlassian ecosystem, the requirement of obtaining ISO 27001 certificate applies to Marketplace Partners that wish to retain their Platinum or Gold partner badge (ref). If you are an Atlassian Marketplace Partner, read more about why you should build your Trust Center in Jira and Confluence.
Once you know your compliance goal, share this information with your team as organisational compliance is a team-effort and needs the buy-in (if not passion and motivation) from everyone.
We have discussed the benefits of ISO 27001 earlier (in our customer case study) but this time we want to describe how you can efficiently prepare for the ISO 27001 audit using a risk-based approach.
Why take Risk-Based Approach to ISO27001?
ISO27001 is about managing and protecting sensitive company and customer data. A risk-based approach to preparing for an ISO 27001 audit involves identifying, assessing, and managing information security risks for each identified information asset. Instead of just following a compliance checklist, it ensures that security controls are implemented based on actual risks faced by the organisation.
A risk-based approach has several advantages:
ISO 27001 is in fact built around risk management (Clause 6.1 – Actions to address risks and opportunities) meaning that organisations must identify security risks and apply appropriate controls to reduce or mitigate them. Risk-based approach aligns naturally with the requirements of the standard.
As ISO27001 certification requires a risk-based ISMS (Information Security Management System), implementing a risk-based approach not only ensures that you meet the standard’s requirements but it also demonstrates a justifiable security strategy in your organisation. This, in turn, improves the overall audit-readiness of your organisation as well as the auditor’s confidence in your ISMS.
Above all, a risk-based approach helps identify and mitigate real security risks that could impact your organisation, ensuring that your security efforts are relevant and effective rather than just fulfilling compliance requirements. It also makes it easier to justify control selections based on actual risks rather than arbitrarily implementing Annex A controls.
Build your Asset-Based Risk Register in Jira
Following the risk-based approach to prepare for your ISO27001 audit, you should start with creating an asset-based risk register in Jira to protect your organisation’s most critical assets.
An asset-based risk register is a structured document used to identify, assess, and manage risks related to specific information assets within an organisation. It helps organisations systematically track risks to ensure that appropriate security controls are implemented, aligning with ISO 27001 requirements.

Step 1: Identify which assets will be covered in your ISMS
You can use Jira Assets for listing and describing your organisation’s information assets (and departments, processes, and locations) or your can use the built-in repository of the SoftComply Risk Manager Plus app.
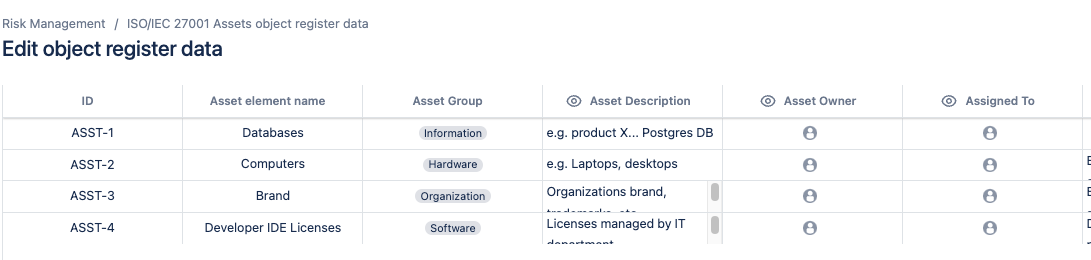
When describing your critical information assets, be sure to include at least the following organisational assets you have:
-
Data (customer records, financial data)
-
Hardware (servers, laptops, networking devices)
-
Software (CRM systems, HR applications)
-
People (employees, vendors, contractors)
-
Processes (data handling, user access control)
Finally, assign ownership to each asset.
Step 2: Conduct Risk Assessment in Jira
You can use the ready-made ISO27001 risk model and risk register templates in the Risk Manager Plus app to speed up your information security risk assessment in Jira. You can customise the risk model to match your risk criticality level.
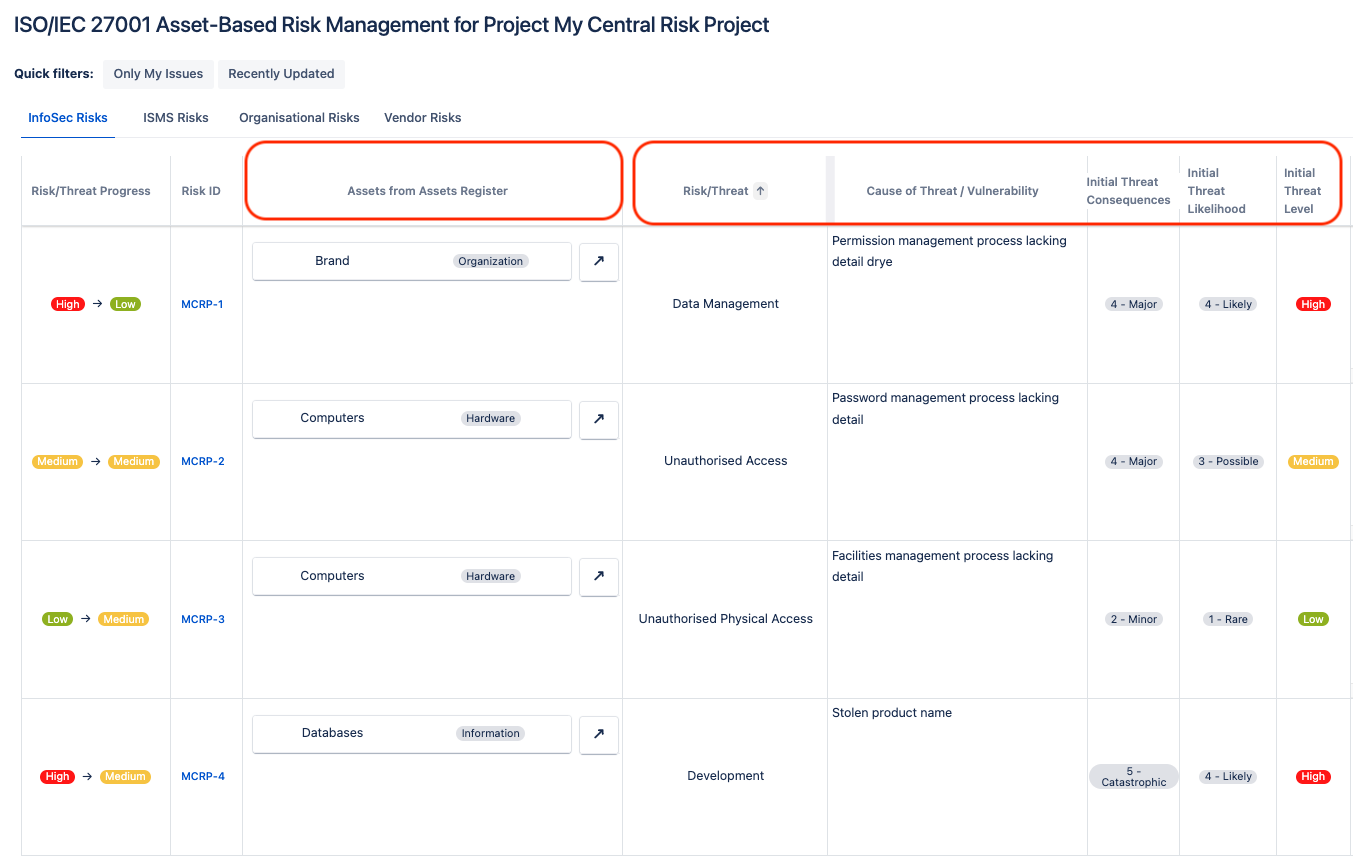
Next, identify and analyse security vulnerabilities and threats for each identified information asset directly in your asset-based risk register view. Once the vulnerabilities and threats have been linked to assets, you can determine the impact and likelihood of each risk occurring to generate a risk score.
Step 3: Implement Risk Controls
In the case where a risk is on a critical level, you will have to mitigate the risk. There are different ways to do it like implementing security controls (choose one from Annex A), transferring it to an external security provider, or changing your processes to lower the risk.
In the SoftComply Risk Manager Plus, you have built-in controls from ISO 27001 that you can pull directly to your asset-based risk register to link it with the identified risks.

Prepare for the ISO27001 Audit
Once you have built your asset-based risk register and work with risk mitigation, you can use a traceability matrix to ensure that all critical risks have been covered by controls so nothing has been overseen.
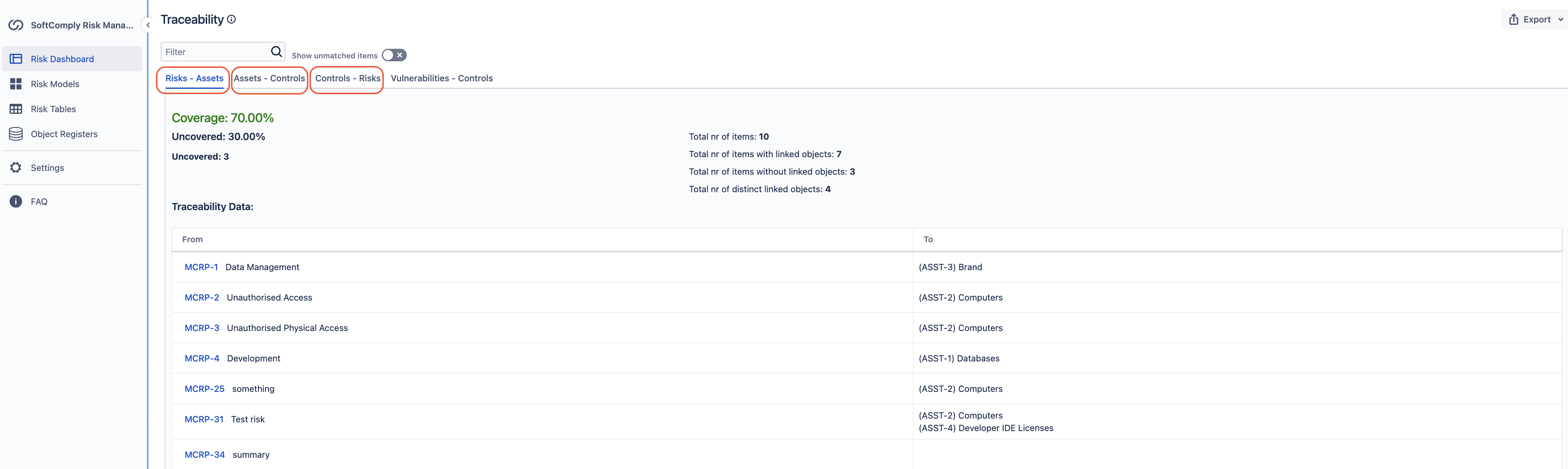
Once all ISO27001 controls have been analysed and applied (or justified when not applied), you can generate the Statement of Applicability.

If you are managing your ISMS documentation, incident report plans and security policies in Confluence, make sure to have your risk reports there as well. In other words, you can display your asset-based risk register also in Confluence.
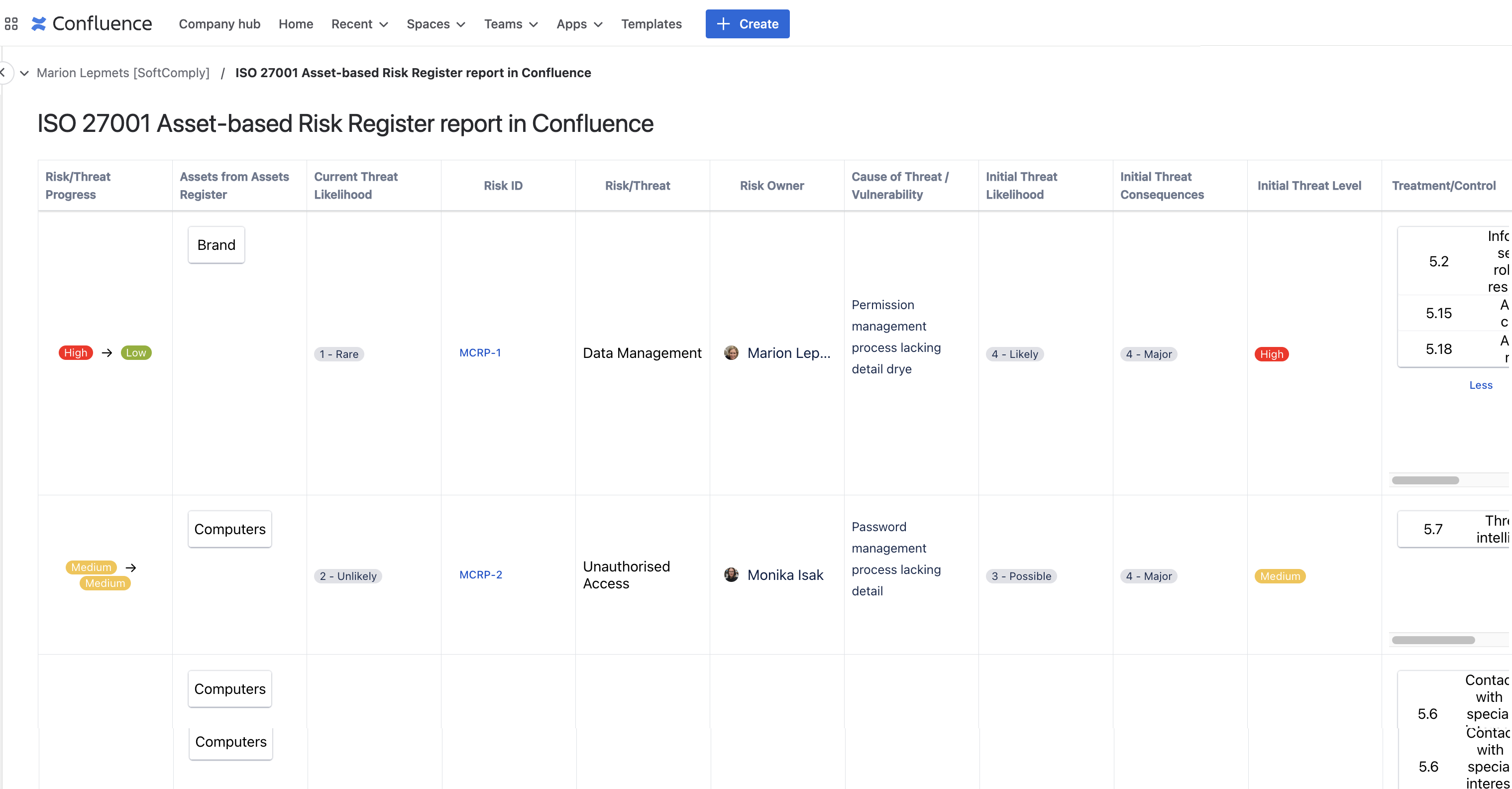
Conclusion
Risk-based approach provides the most efficient way to manage and protect your organisation’s critical information assets, and prepare for ISO 27001 certification.
Preparing for ISO27001 with a risk-based approach inside Jira supports the collaborative effort towards your organisation’s certification. It also provides seamless integration with your organisation’s assets, be they issues in another Jira project, in Jira Assets or in the built-in repositories of the SoftComply Risk Manager Plus app.
With the Risk Manager Plus app, you can choose built-in templates for your Risk Model – the basis of your risk assessment. You can also use the built-in asset-based risk register that is based on ISO 27001 where you can easily link your assets to threats and vulnerabilities, assess the risks and choose the applicable controls from ISO 27001 that are also provided within the app.
Bonus: Risk Manager Plus on Jira Cloud is free for all Atlassian Solution Partners
Want to learn more about it? Schedule a call with our team!






