The Role of Cybersecurity in Medical Device Safety
The Global medical device market is a $800 billion business that is rapidly growing, especially in the area of software as a medical device (SaMD). The majority of the SaMD segment is made up of the digital health and digital therapeutics solutions, where medical devices are made solely of software.
Medical Device manufacturers are facing significant challenges in complying with various regulations and their requirements. A MedTech Company must be compliant with their regional safety, performance and security regulations prior to placing their products on the market. This is a huge bottleneck for SMEs (that form 90% of the medical device market) in getting their innovative products to market fast since compliance is both an extremely time-consuming and very costly process.
SoftComply has built an advanced risk management solution on Jira Cloud for the medical device developers to speed up compliance and time to market of the medical innovations. Now the risk management solution that’s been built for safety risk management of the complex software systems has been extended to support meeting various cybersecurity regulatory requirements as well.
Cybersecurity Requirements in the EU and the US
The aim of cybersecurity regulations is to design security (and prevent the any impact on safety) into the medical device early on as opposed to having it as an afterthought or manual exercise.
Medical device developers in the US have to comply with the FDA Cybersecurity Guidance documents that refer to the widely recognized cybersecurity framework such as the NIST Cybersecurity Framework, specifically the NIST 800-53 and NIST 800-30. These documents describe the methods the medical device manufacturers need to apply to identify and assess possible threats to and vulnerabilities of their products. The preferred risk evaluation method is the well-known Common Vulnerability Scoring System (CVSS), recommended by both the FDA and the MDCG; and the frameworks list of controls that must be put in place to mitigate the risks. Currently, it is accepted that compliance with the US requirements (FDA) adequately covers also the EU market.
Nevertheless, the medical device regulations (MDR and IVDR) in the EU have their own cybersecurity extension that is described in the MDCG 2019-16 “Guidance on cybersecurity for medical devices” which the European medical device developers have to comply with.
FDA Cybersecurity Guidance
The FDA Guidance “Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions” from 2023, contains a well defined list of recommended controls in Appendix I, neatly grouped by area:

If you are familiar with how the FDA operates, these “recommendations” are pretty much “must-do” unless you have a good rationale. Being able to demonstrate that you have considered all of them can prevent delays in the review of the your device submissions.
FDA Cybersecurity Guidance refers to the CVSS and NIST Cybersecurity Framework for risk assessment and additional set of controls.
NIST Cybersecurity Framework (CSF)
NIST CSF is a must if you are planning to enter the US governative market.
The NIST Special Publication (SP) 800 series applies to US federal agencies, organizations and their suppliers/subcontractors when contractually obligated to do so. There are two publications in the series that are widely used for cybersecurity risk assessment (NIST SP 800-30) and for risk controls (NIST SP 800-53) and recognized by other cybersecurity frameworks.
NIST SP 800-53
This NIST Special Publication is a list of Controls. 2000+ items to be considered if a Company intends to follow the NIST model to the letter. They are well organized, each with its own unique ID.
NIST SP 800-30
The purpose of the Special Publication 800-30 is to provide guidance for conducting information security risk assessments by providing detailed process description and risk assessment (risk model) steps.
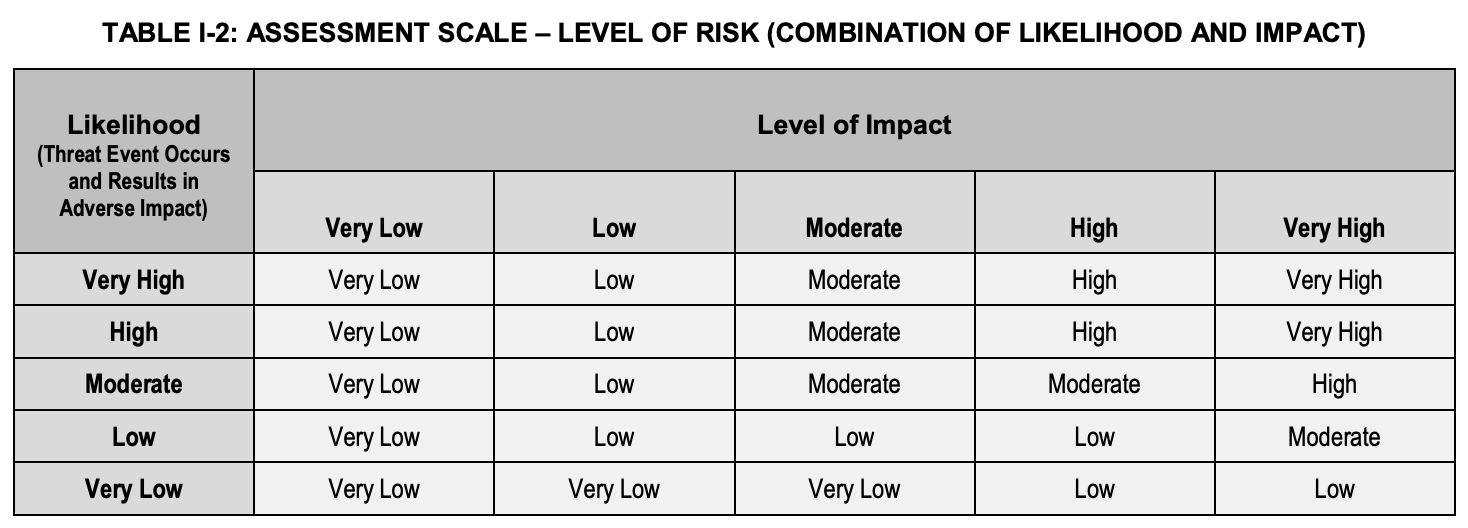
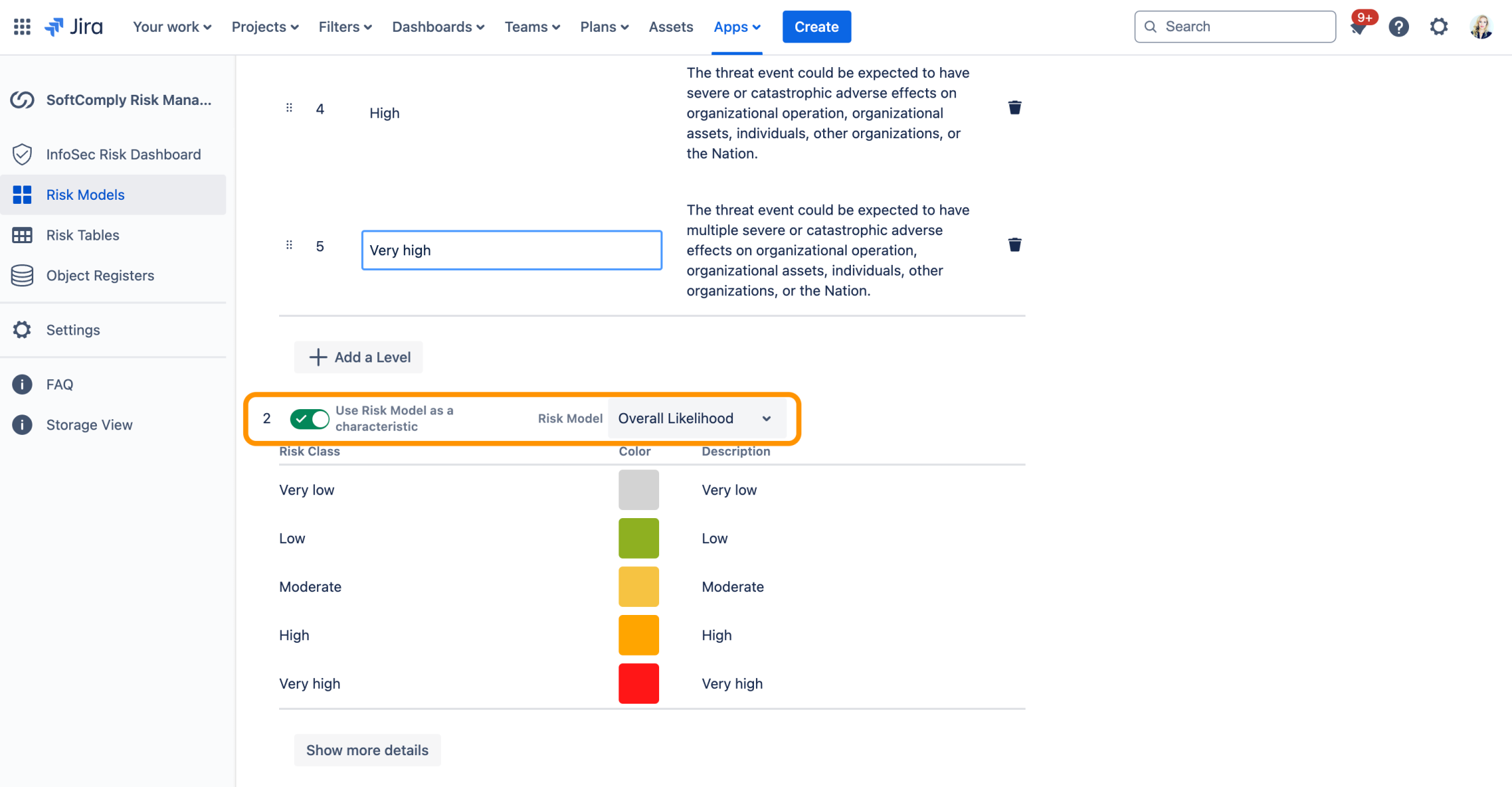
The top-level risk model is described in the Annex I of NIST 800-30 Table I-2, and it is a combination of “Likelihood” and “Level of Impact”, in a 2D matrix.
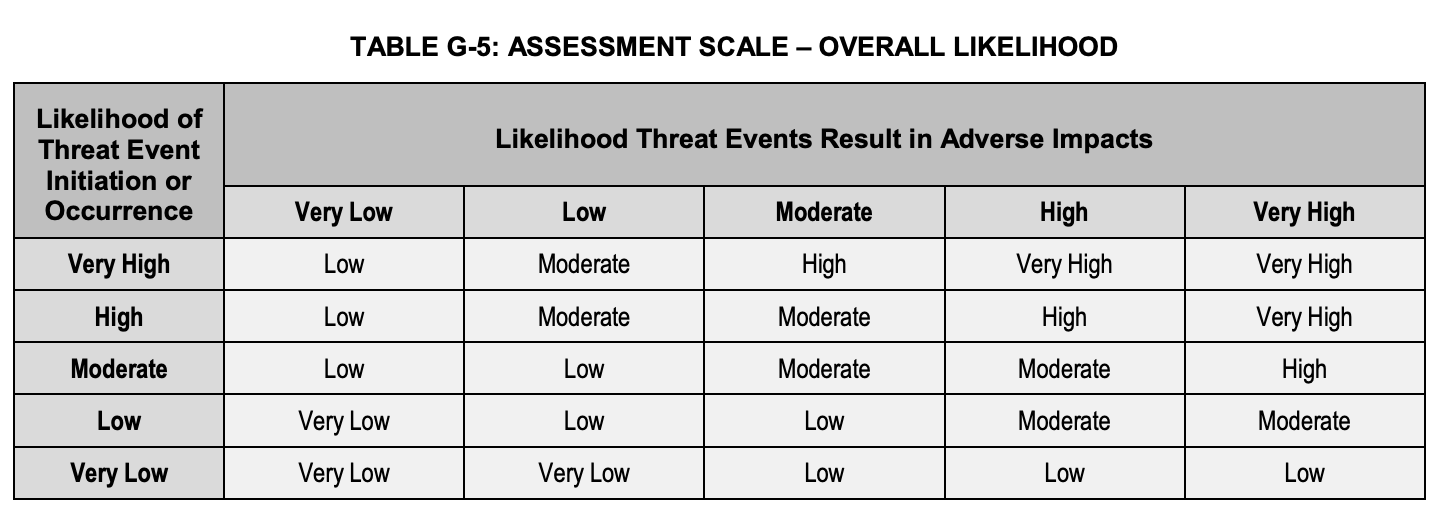
The likelihood itself is calculated as Overall Likelihood as shown in Table G-5, that is a combination of “Likelihood of Threat Event Initiation or Occurrence” and “Likelihood of Threat Events Resulting in Adverse Impacts”:
In a simplified way, NIST 800-30 uses 3 parameters in their Risk Models:
- Likelihood of Threat Event Initiation or Occurrence
- Likelihood of Threat Events Resulting in Adverse Impacts
- Impact
but the first two are combined into an Overall Likelihood before being used to determine the Risk Level.
“Likelihood of Threat Event Initiation or Occurrence” and “Likelihood Threat Events Resulting in Adverse Impacts” are characteristics nested underneath the top-level risk model.
NOTE: Now, you can build these complex Risk Assessment scenarios easily using the Risk Manager Plus Parent > Child Nested Risk Models.
Common Vulnerability Scoring within a Jira Issue – CVSS 4.0
CVSS 4.0 uses up to 32 metrics to calculate the CVSS score. These metrics are combined into a single value, the CVSS score itself.
The base metrics are usually provided by the developer, while each company can further score the vulnerability according to the specific internal application and use.
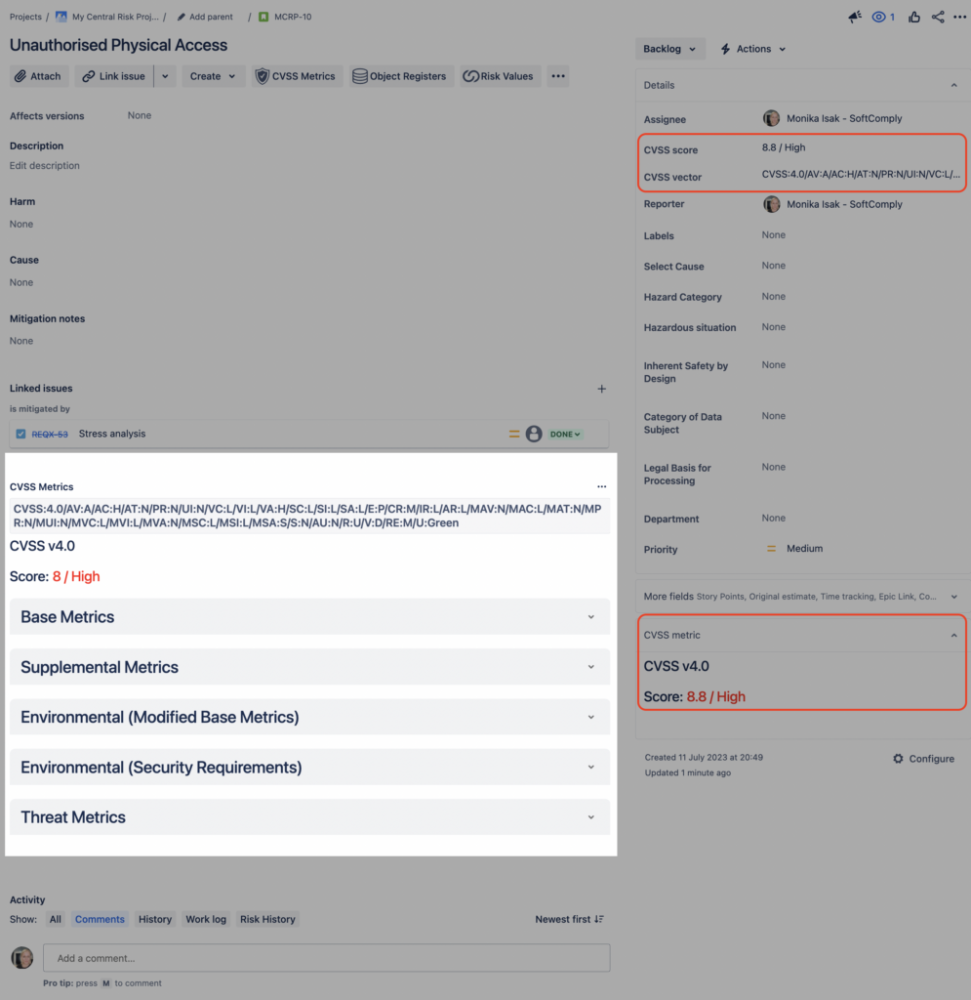
Using the Risk Manager Plus, you can now score the vulnerabilities directly in your Jira issue view. All metrics are there for you to assess. The final score will be calculated automatically, giving you a colour-coded criticality level and the CVSS vector, helping you to plan further activities to deal with the vulnerabilities.
To simplify the overview of visualising the overall status, you can use the CVSS scores also in the Risk Table view, where the colour coding will help you to prioritise across all of the assessed vulnerabilities.
NOTE: You can read more about assessing your security vulnerabilities using the CVSS in Jira in our earlier blog post.
MDCG 2019-16
This EU guidance document “Guidance on Cybersecurity for medical devices“ contains a number of recommendations how medical device developers can protect against unauthorised access and possible cyber threats. These recommendations are scattered over the whole document, some in a handy bulletpoint list format and some more as free text. Being able to find, list and trace them to the Risk Analysis documents is a significant Compliance (and practical) advantage in itself.
NOTE: These recommendations of controls have been added to the Risk Manager Plus in Jira to be used during the cybersecurity risk management.
New Cybersecurity Risk Management Features in Jira
The new risk management features supporting NIST Cybersecurity Framework (CSF), FDA and MDCG Cybersecurity Guidance and CVSS frameworks have been implemented in the SoftComply Risk Manager Plus so that the regulated industry companies can design safety and security easily into their product.
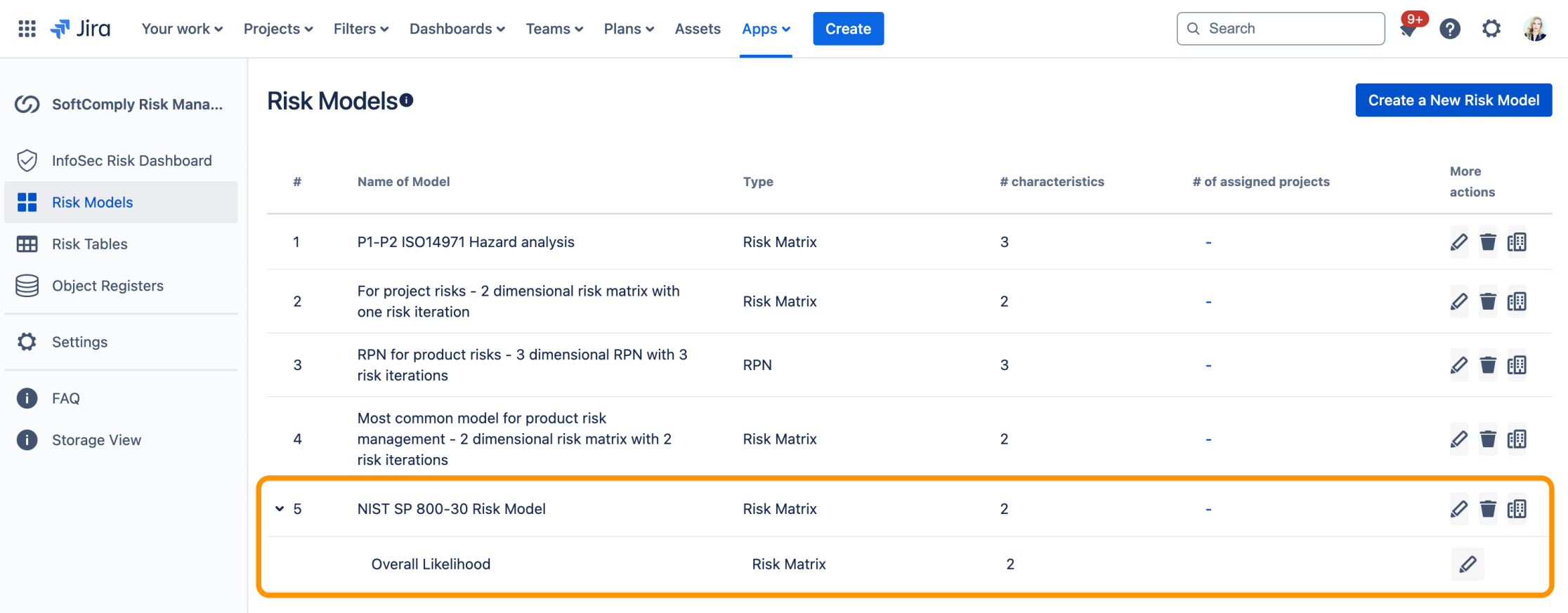
Advanced Risk Models for NIST CSF in Jira
Typical risk assessment models include 2 or 3 risk characteristics, that are then combined together to determine the risk level. For example, a Risk Level or Risk Score can be calculated based on the values of Probability and Severity; Probability, Severity and Detection; P1xP2 and Severity.
However, in certain scenarios, the risk level is calculated using a significant number of risk characteristics, where some of the characteristics need to be combined into a single value (“nested” characteristics), which is then used for the final risk score (a bit like P1xP2, but more complex). This may be required due to the complexity of the sequence of events, or more simply because the company is following some National or International Cybersecurity Framework like NIST or CVSS.
In the example below, the Risk Characteristics 1, 2 and 3 are combined to calculate “Characteristic 4”. Characteristic 4 is then used in the top-level model together with characteristic 5 and 6 to calculate the Risk Level:
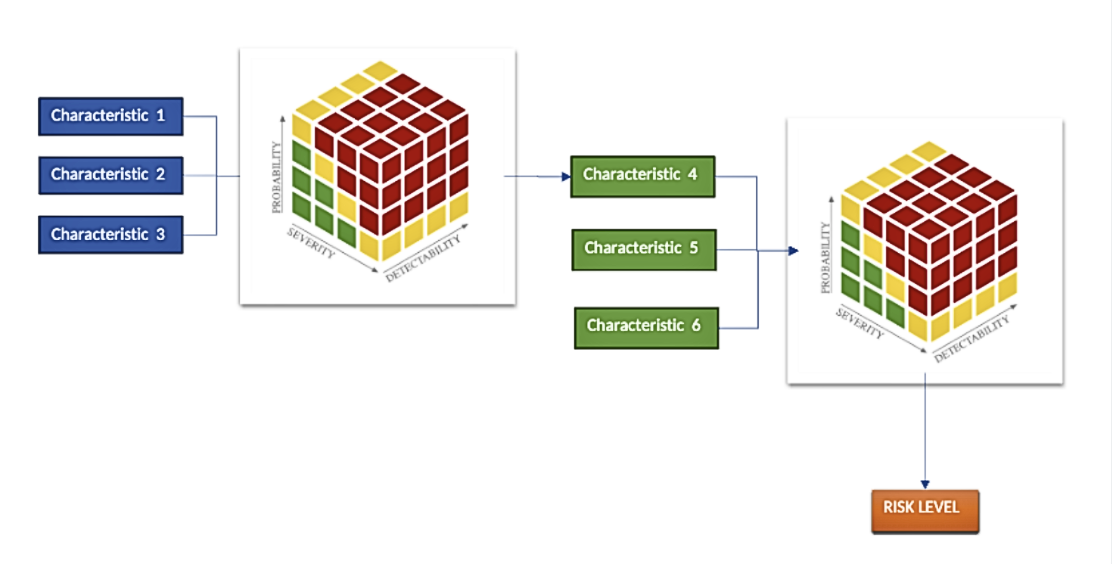
You can now build these complex Risk Assessment scenarios supporting NIST 800-30 using the Risk Manager Plus app shown below where you can create Child and Parent Risk Models:
CVSS in Jira
Using the Risk Manager Plus, you can now score the vulnerabilities directly in your Jira ticket. All metrics are there for you to assess. The final score will be calculated automatically, giving you a colour-coded criticality level and the CVSS vector, helping you to plan further activities to deal with the vulnerabilities.
To simplify the overview of visualising the overall status, you can use the CVSS scores also in the Risk Table view, where the colour coding will help you to prioritise across all of the assessed vulnerabilities.
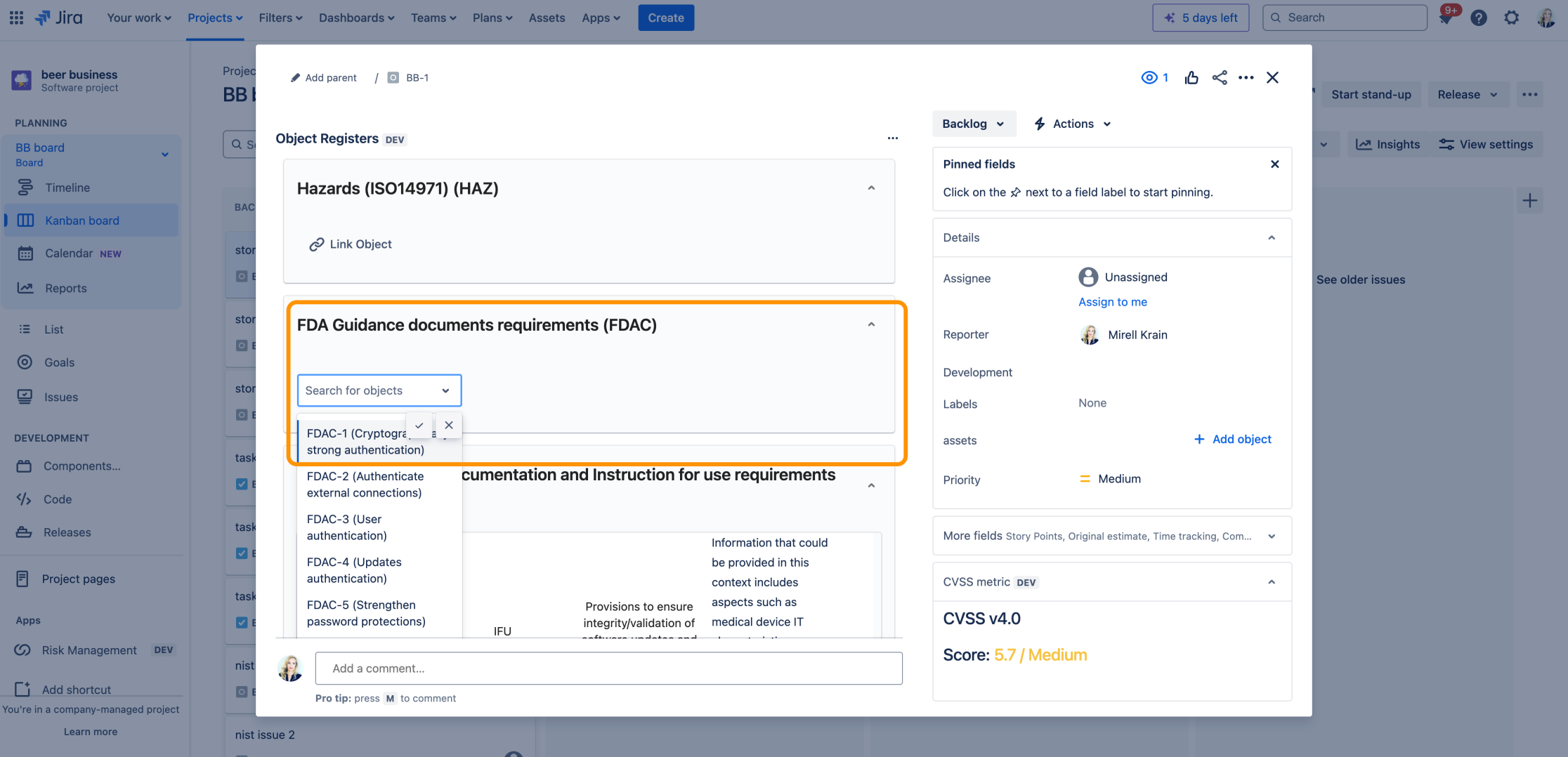
FDA Cybersecurity Controls in Jira
The Risk Manager Plus app helps organizations apply various FDA Cybersecurity Guidance documents to ensure compliance with these regulatory requirements. The app provides users with a list of FDA cybersecurity controls, which can be linked to risk projects and integrated with risks and other Jira issues. This enables traceability between FDA Cybersecurity Guidance Cybersecurity: Quality System Considerations and Premarket Submissions , its requirements, and Jira issues, supporting comprehensive compliance and effective risk management.
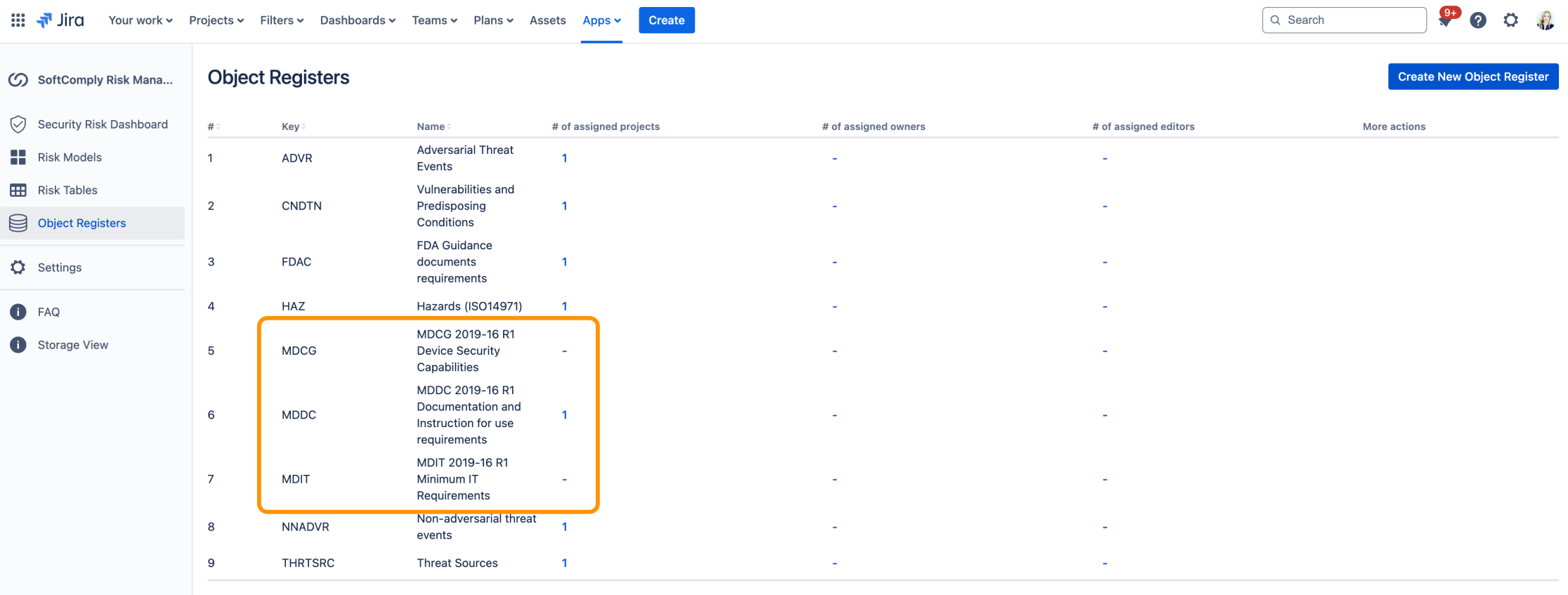
MDCG Lists of Requirements in Jira
The Risk Manager Plus app assists organizations in applying various documents provided by MDCG 2019-16 to comply with the MDR and IVDR regulations.
The app offers three distinct MDCG requirements libraries, which can be linked to a risk project and their associated with risks. This enables the creation of traceability between MDCG items and risks to monitor the coverage with MDCG requirements.
The app includes three MDCG libraries: MDCG 2019-16 R1 Device Security Capabilities, MDCG 2019-16 R1 Documentation and Instructions for Use Requirements, and MDIT 2019-16 R1 Minimum IT Requirements.
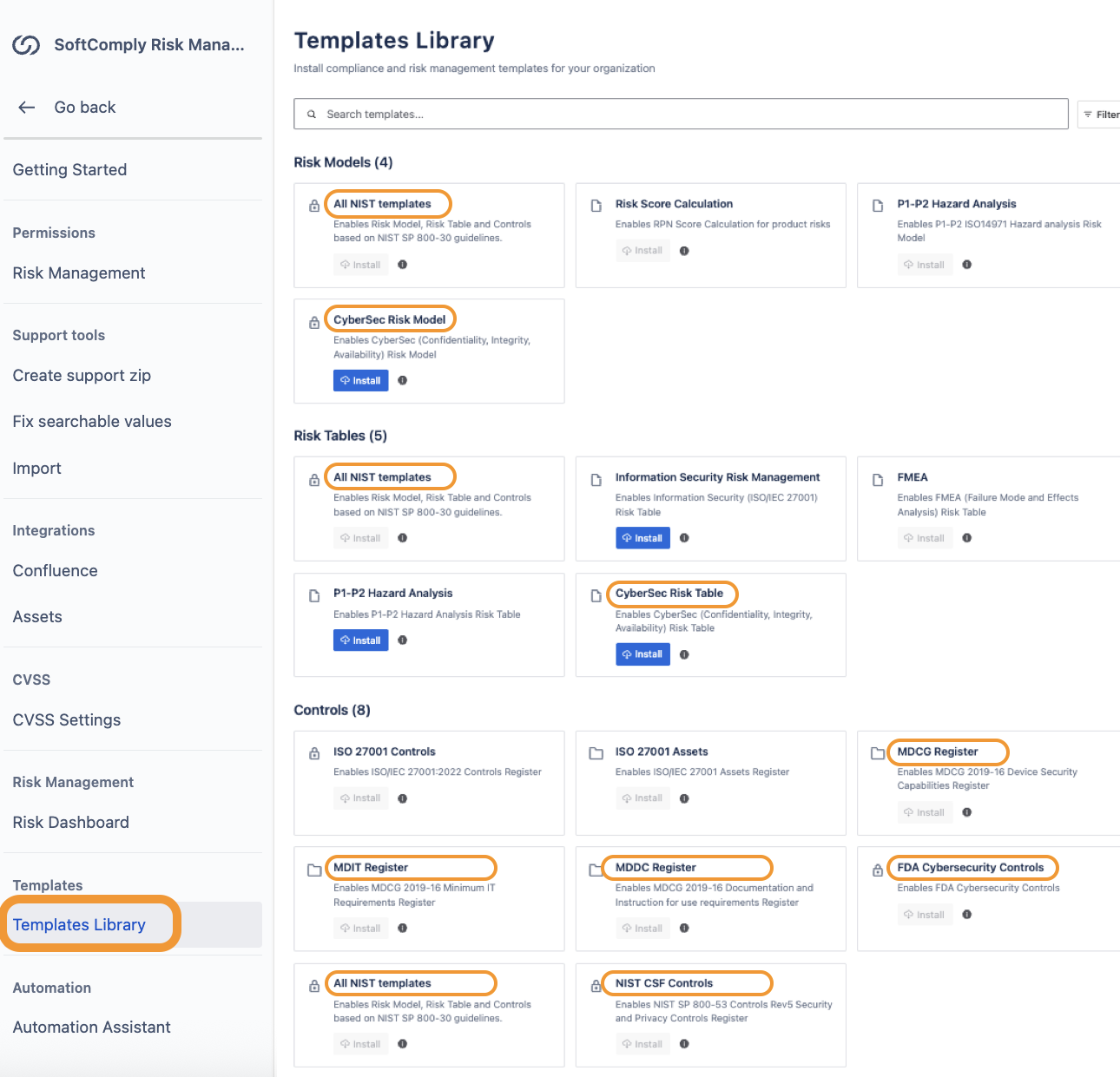
Templates Library for Cybersecurity Risk Models, Risk Registers and Risk Controls
We have implemented a list of required templates within the Risk Manager Plus app that you can start using based on your specific need.
You can choose to enable the risk model or risk table for the NIST CSF, or lists of controls for NIST CSF, FDA Cybersecurity or MDCG Guidance.
Cybersecurity Risk Management Templates in Jira
Traceability Matrix for Risk Coverage
Traceability is vital for risk management giving you the chance to monitor the coverage between your information assets and risks; threats, risks and controls; and so forth.
You can now set up traceability items that you would like to see the coverage of inside the app.
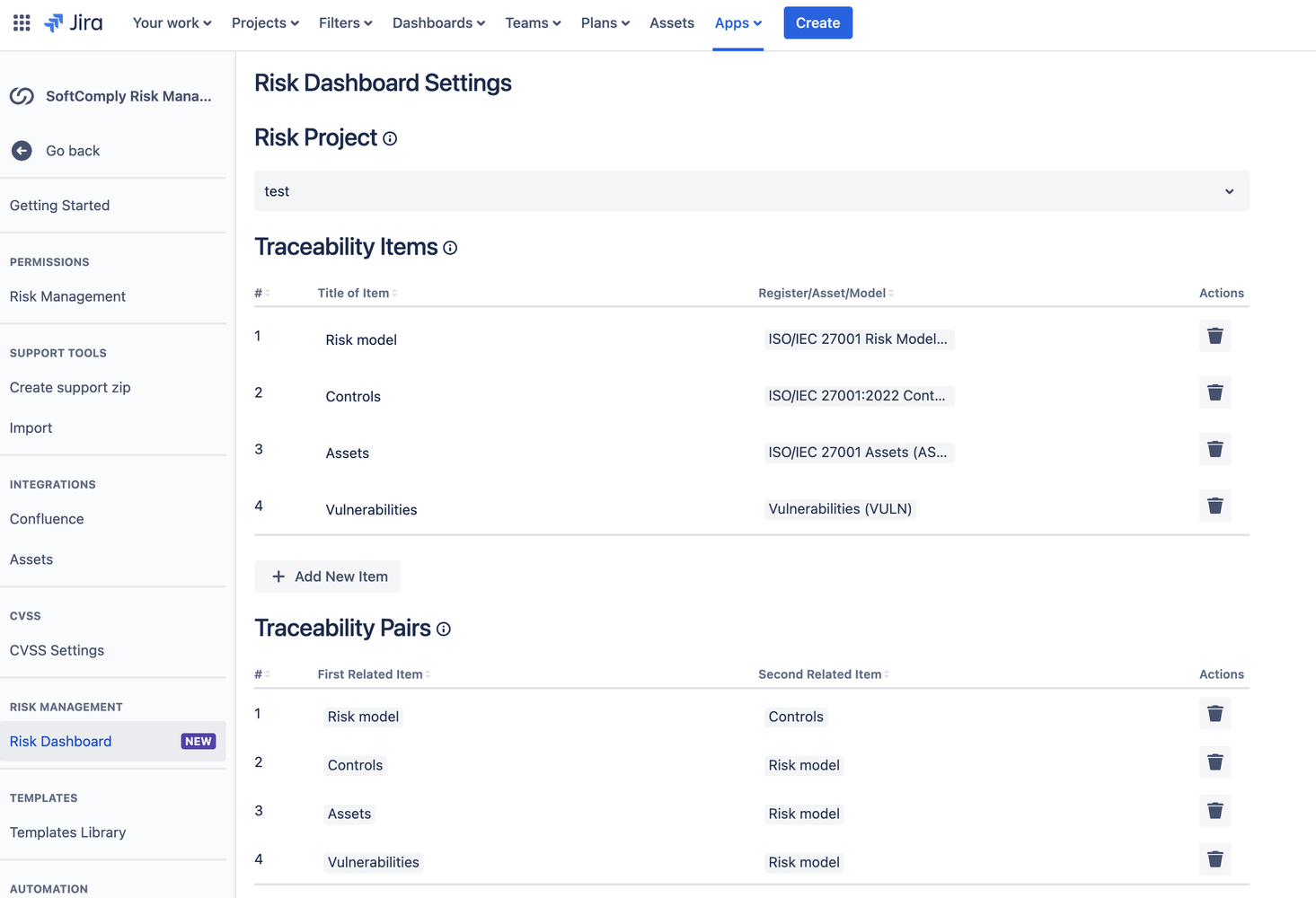
Traceability Matrix Setup in Jira
Once the pairs have been set up, you can view the coverage percentage between the items and filter these as needed.
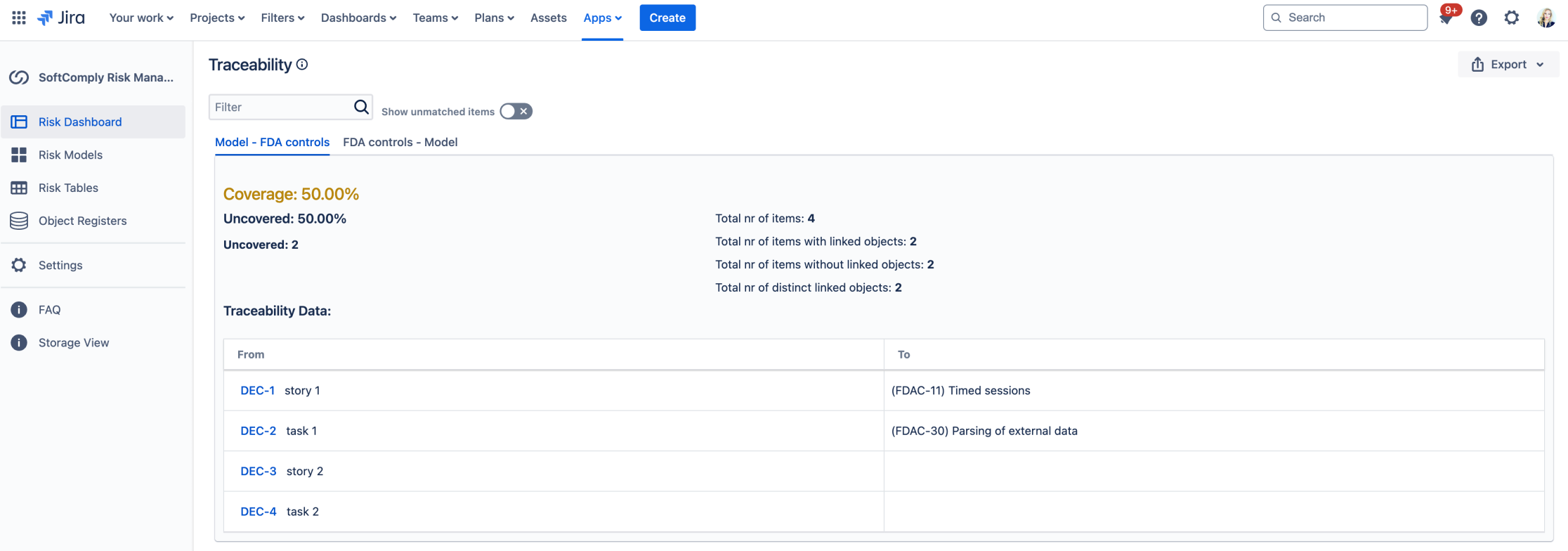
Traceability coverage report between risks and FDA controls







