What is Information Security Risk Management?
Information security risk management is a systematic process that involves identifying, assessing, prioritizing, and mitigating potential risks that could compromise an organization’s information assets. These assets may include customer data, intellectual property, financial information, or proprietary business processes. The risk management process allows companies to maintain confidentiality, integrity, and availability of their information, protecting it from unauthorized access, modification, or destruction.
ISO/IEC 27001 is an internationally recognized standard for information security management systems (ISMS). It provides a framework that helps companies establish, implement, maintain, and continually improve their information security risk management processes. To comply with ISO/IEC 27001, organizations must follow these key requirements:
a. Risk Assessment: ISO/IEC 27001 mandates a thorough risk assessment, which includes identifying assets, evaluating threats and vulnerabilities, and assessing the potential impact. This process aids in prioritizing risks and determining appropriate controls.
b. Information Security Policy: Companies must establish a comprehensive information security policy that outlines their commitment to risk management, sets objectives, and defines the roles and responsibilities of employees regarding information security.
c. Risk Treatment Plan: ISO/IEC 27001 requires organizations to develop a risk treatment plan, which includes selecting and implementing controls to mitigate identified risks effectively. The plan must be tailored to the organization’s specific needs and risk appetite.
SoftComply Information Security Risk Manager app on Jira Cloud
SoftComply Information Security Risk Manager supports you in your journey towards compliance with the ISO/IEC 27001.
The SoftComply Information Security Risk Manager app comes with 4 powerful modules:
- Information Security Dashboard – to monitor progress towards ISO/IEC 27001 compliance & check status coverage between assets, risks and controls;
- Risk Model – ready-made risk models that you can customise for your information security risk assessment;
- Risk Table – multi-sheet risk register to identify risks associated to each asset and controls for each identified risk;
- Object Registers – for organisation-wide list of assets and controls.
Information Security Dashboard in Jira Cloud
SoftComply Information Security Risk Manager comes with a powerful Dashboard with a Checklist monitoring your progress towards compliance with the ISO/IEC 27001 as well as a Traceability Matrix indicating the coverage status between assets, risks and controls.
The Information Security Dashboard provides a quick view into the Risk Model used in the project:
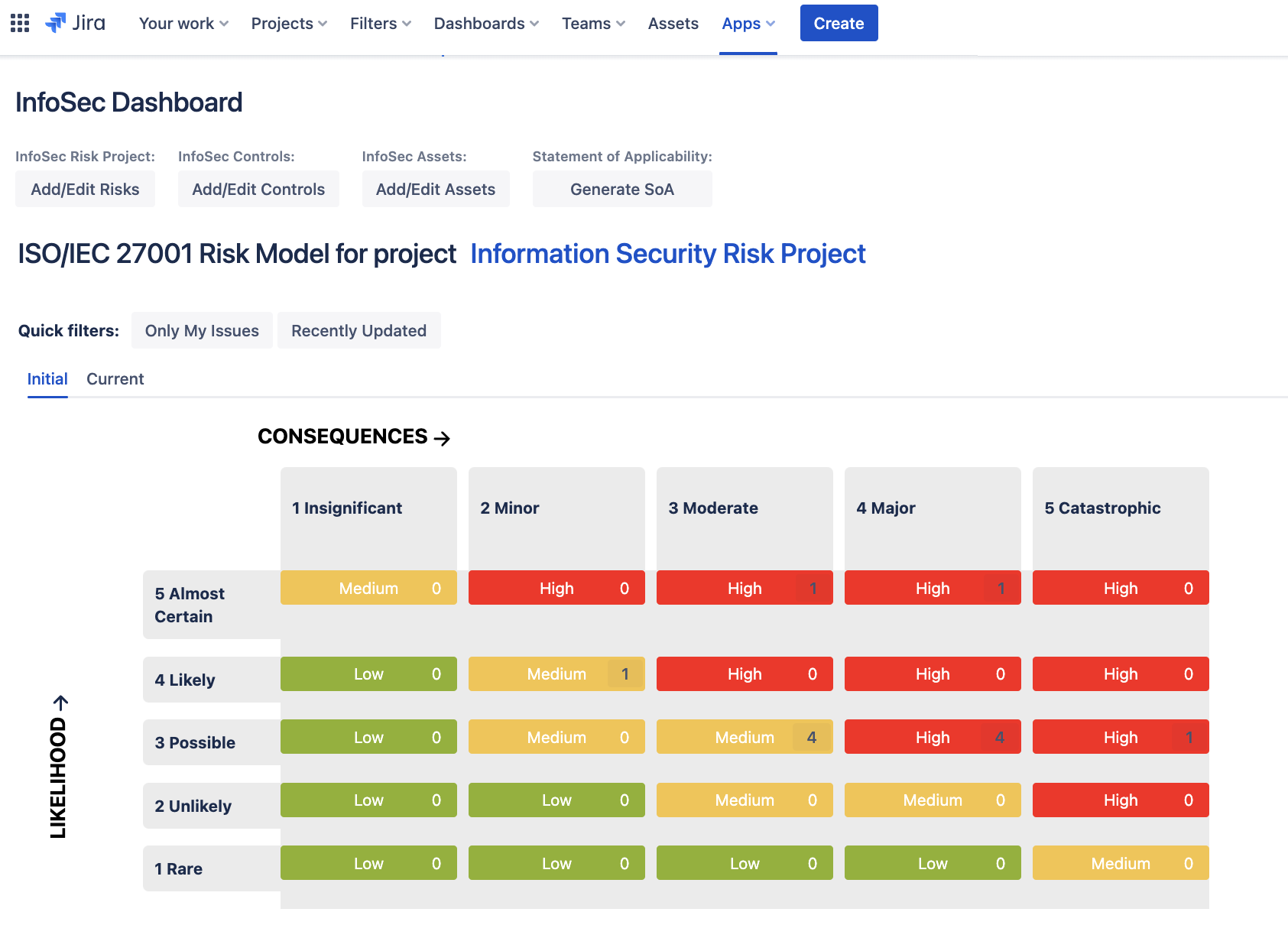
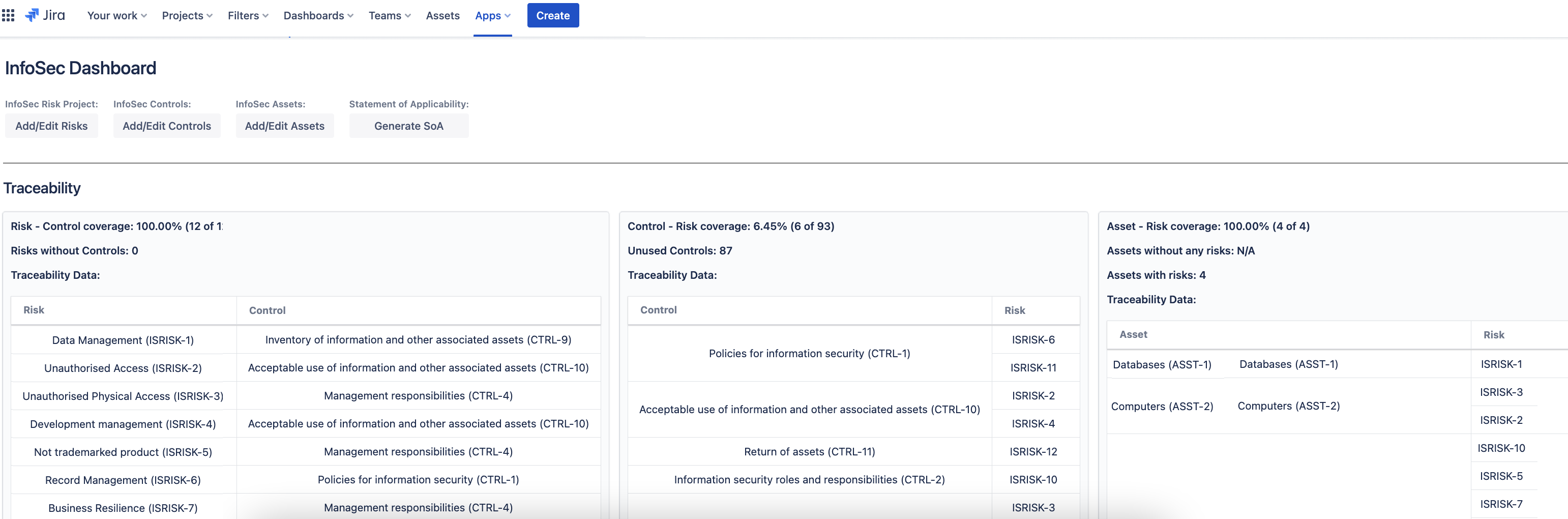
The Dashboard also provides you with a Traceability Matrix indicating the Status of Coverage between assets, risks and controls throughout the project. You can also generate your Statement of Applicability automatically from the Dashboard:
You can use the ISO/IEC 27001 Checklist to monitor your compliance progress of ISO/IEC 27001 Requirements in the Information Security Dashboard:

Risk Models – customizable Risk Models for Information Security Risk Assessment
SoftComply Information Security Risk Manager comes with 3 Global Risk Model templates that you can further customise: two templates for 2-dimensional Risk Matrices and one Risk Model for RPN (Risk Score) based risk assessment. You can further customize these templates based on the risk model used in your organisation.
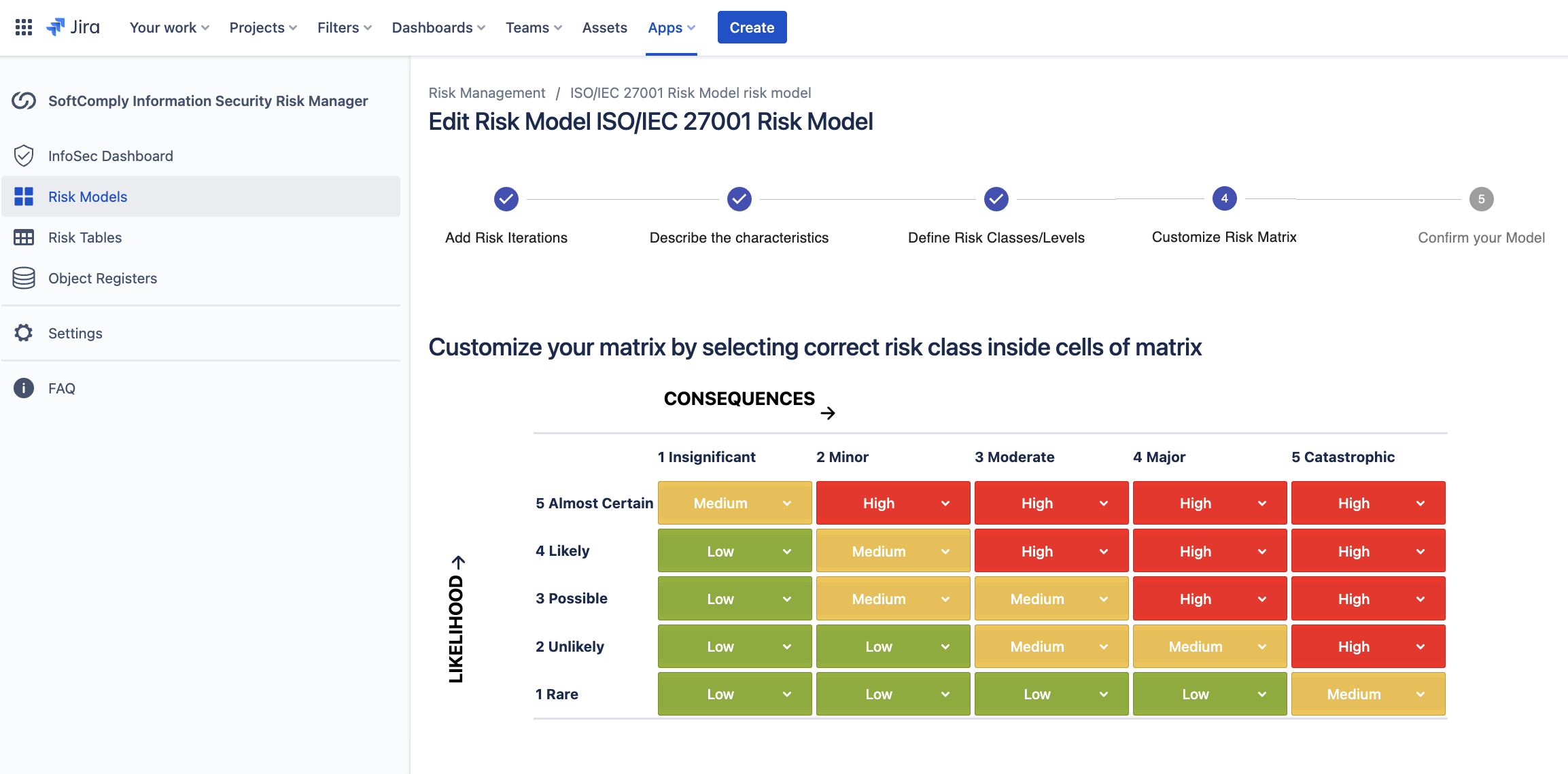
Asset-Based Risk Management Table – multi-sheet Risk Register for working with Assets, Risks and Controls
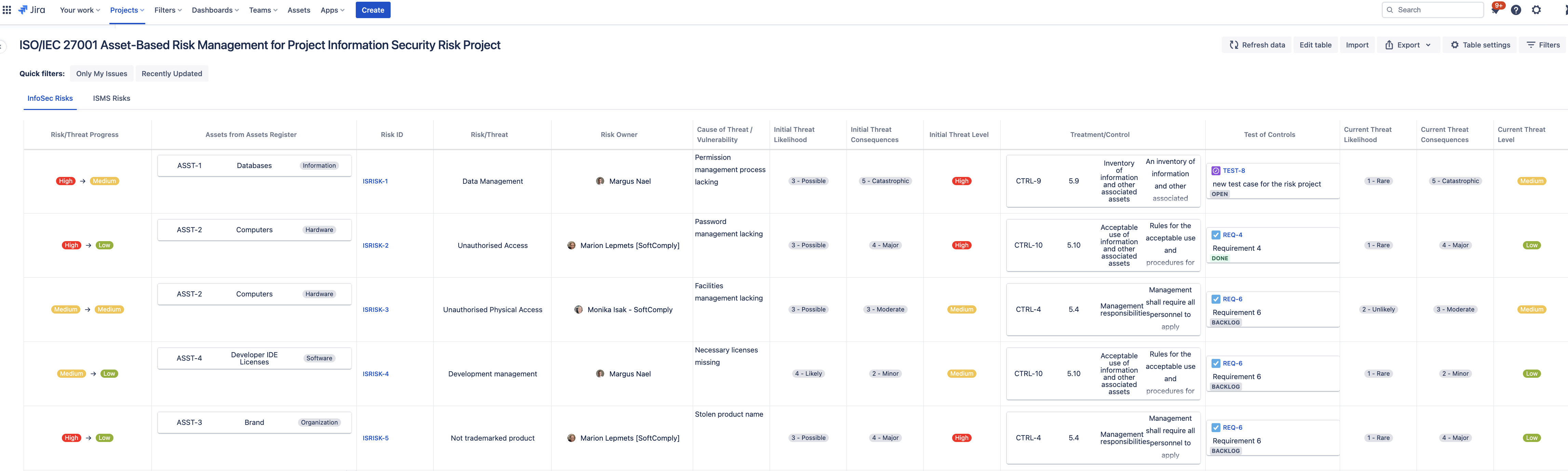
SoftComply Information Security Risk Manager provides you with a ready-made Risk Register for ISO/IEC 27001 Asset-Based risk management. The table has 2 sheets – one for managing Information Security Risks and the other to manage ISMS related tasks.
In the asset-based risk table you can choose the assets and controls from your organisation-wide libraries while identified their related risks. You can also describe the risks and assess them.
Object Registers for Assets and Controls
In the SoftComply Information Security Risk Manager app, you can define organisation-wide assets in the Object Registers. Your team can simply select the applicable assets in the Risk Register to identify the related potential risks later on.
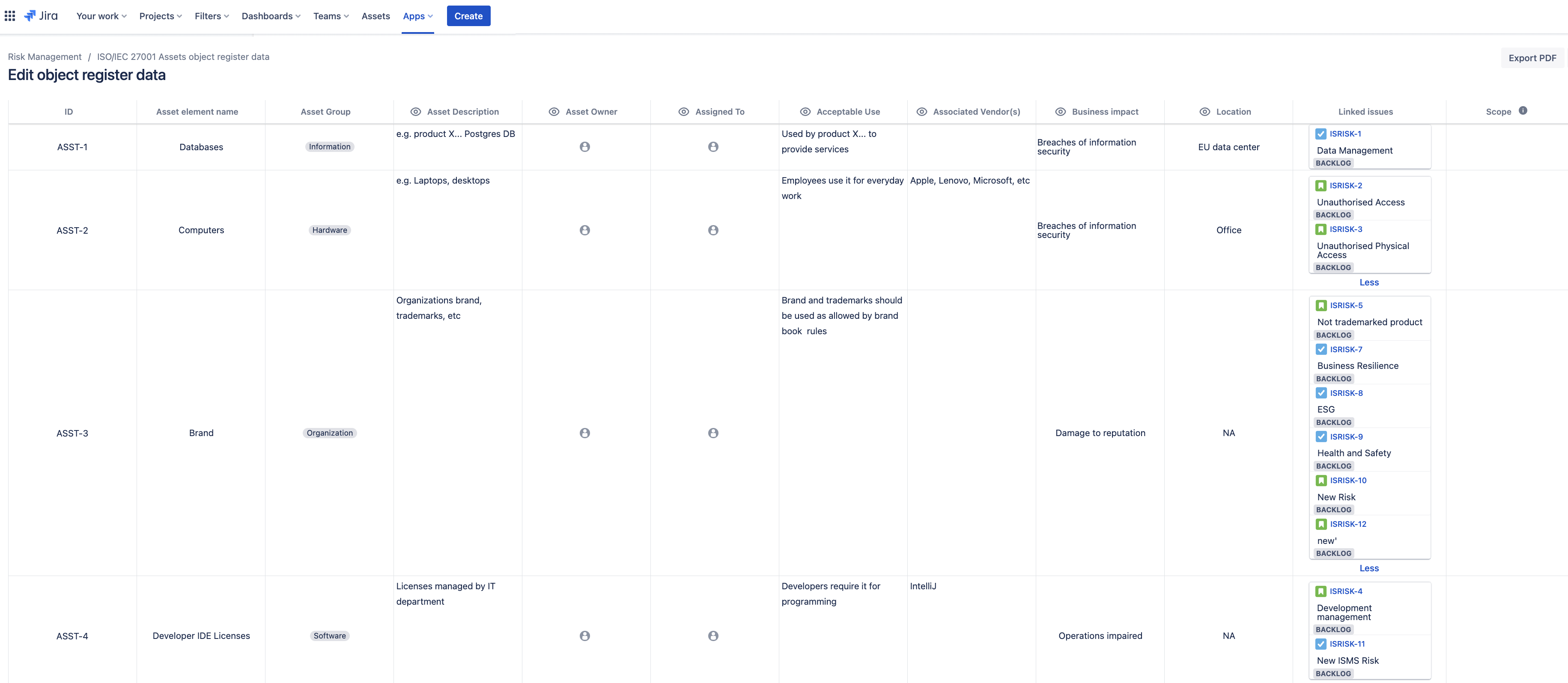
You can also customise the pre-populated library of information security controls based on ISO/IEC 27001. The object registers also display the associated risks for each asset and the controls you have linked to each risk.
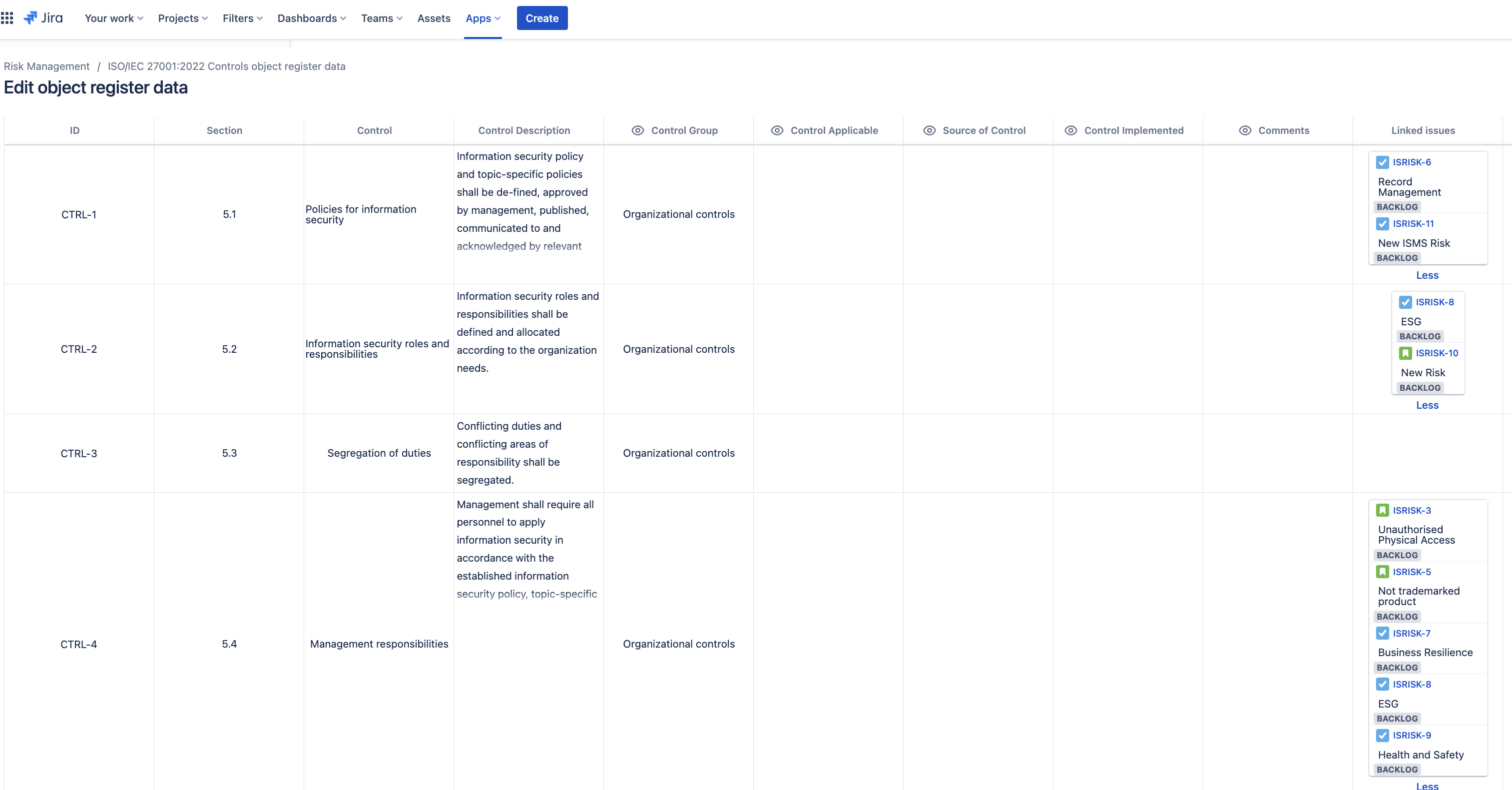
Risk Reports
In order to see if all the ISO/IEC 27001 controls have been applied in the mitigation of the information security risks, you can automatically generate the Statement of Applicability as a web-based and easily shareable document from the Dashboard.
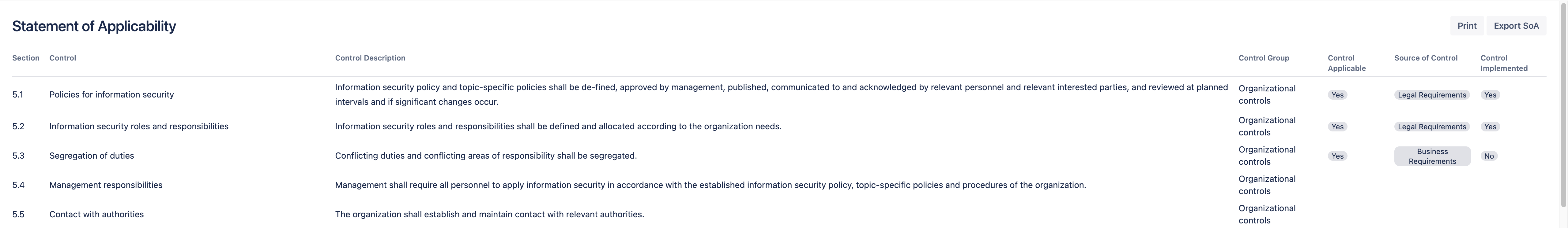
In addition to the Statement of Applicability, you can report your risks in Confluence with the free SoftComply Risk Manager for Confluence app as with all the other SoftComply Risk Manager apps. You can bring both the Risk Register as well as the Risk Model onto your Confluence pages for detailed risk management reports.
How to Learn More
Feel free to try the app out for free for 30 days or book an online live demo of the app with our sales team.
SoftComply Information Security Risk Manager is based on the SoftComply Risk Manager Plus – you can check out the comparison between the SoftComply Risk Management apps here.





